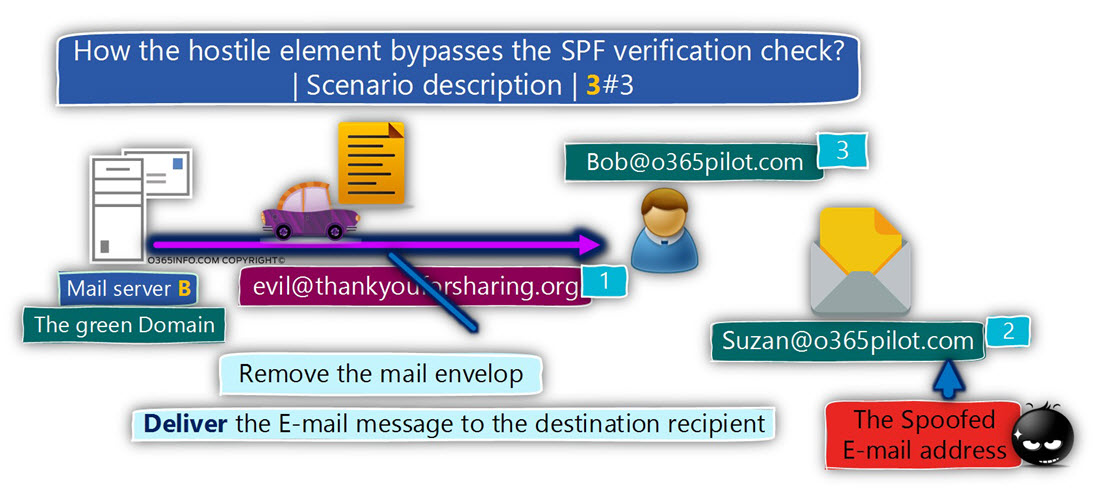
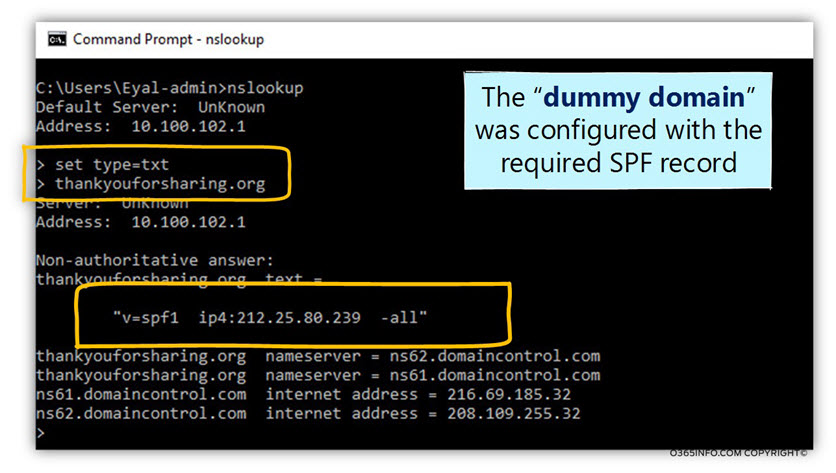
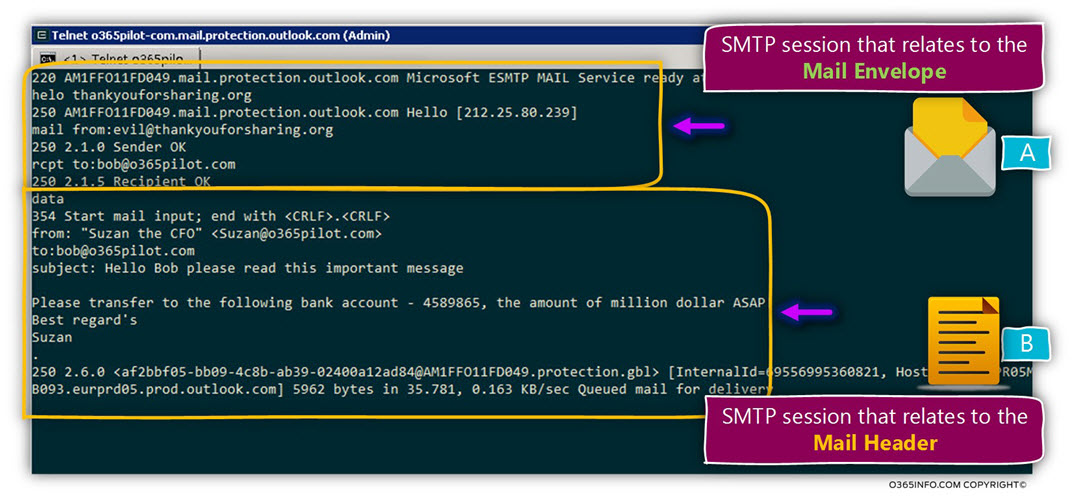
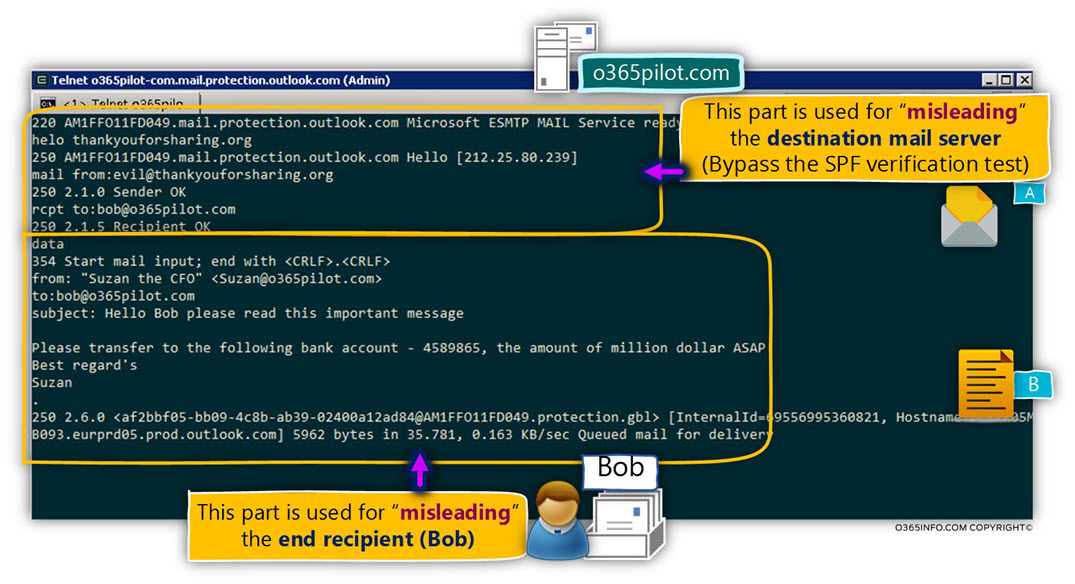
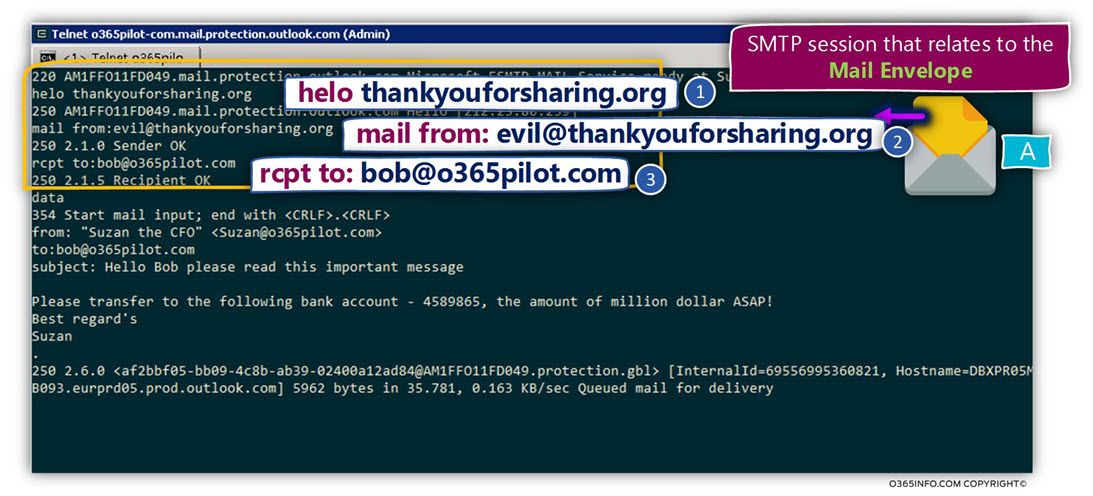
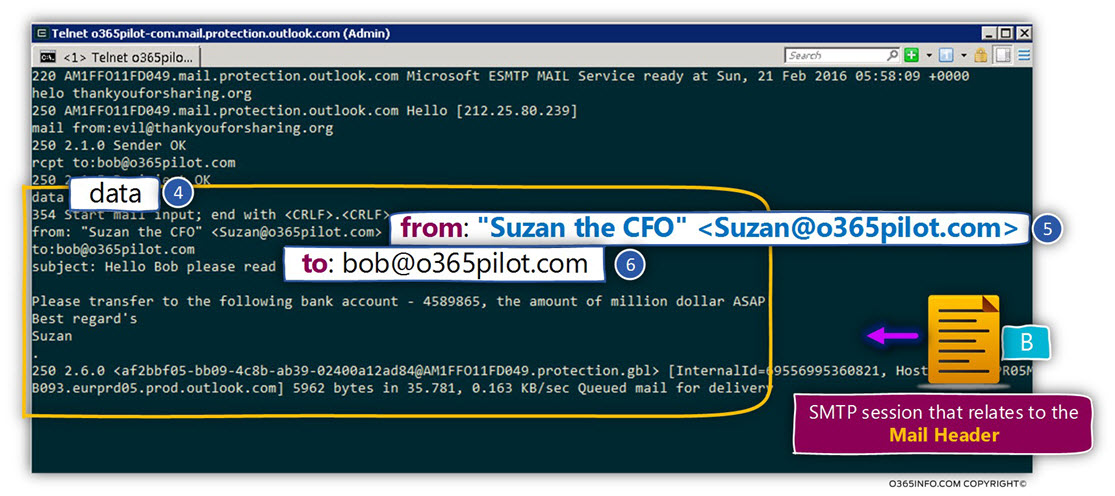
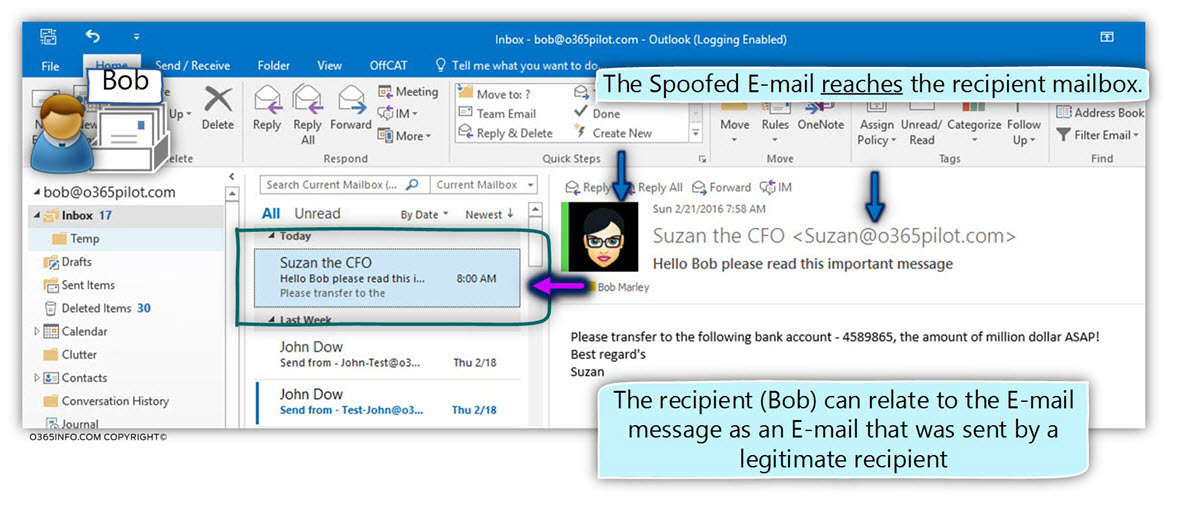
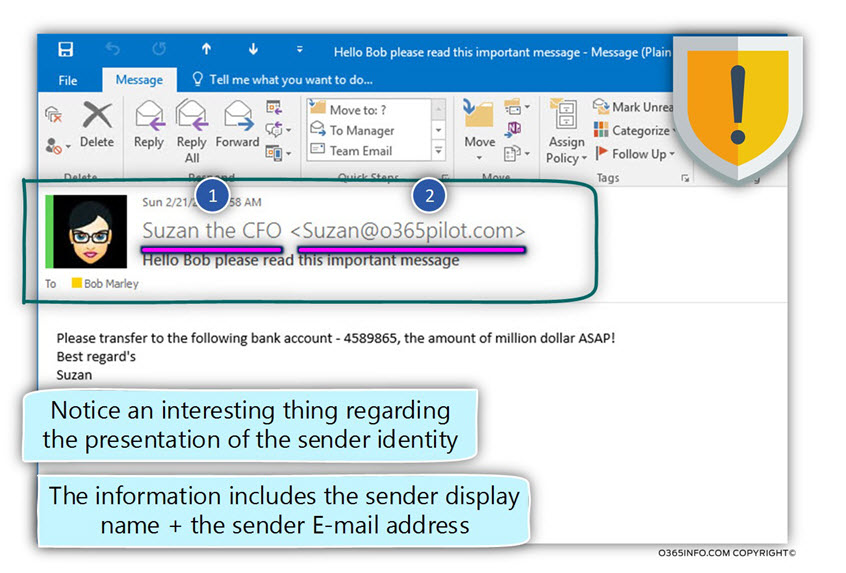
DKIM is implemented by using Digital signature. The “Digital signature” method is one of the main building blocks of the Public key infrastructure.
In the current article, I want to show you a fraction of Interesting and wonderful world of Public key infrastructure and, the way that the DKIM uses this infrastructure for implementing the concept of sender identity.
DKIM in Office 365| Table of content
Implementing DKIM in Office 365 | Article Series
- DKIM – Domain Keys Identified Mail | Basic introduction | Part 1#5
- DKIM as standard that based upon the Public key infrastructure | Part 2#5
- DKIM flow in Office 365 | Part 3#5
- Outbound DKIM signing and DNS infrastructure | Building the required DNS records for Office 365 | Part 4#5
- How to enable outbound DKIM signing for your domain in Office 365 |Part 5#5
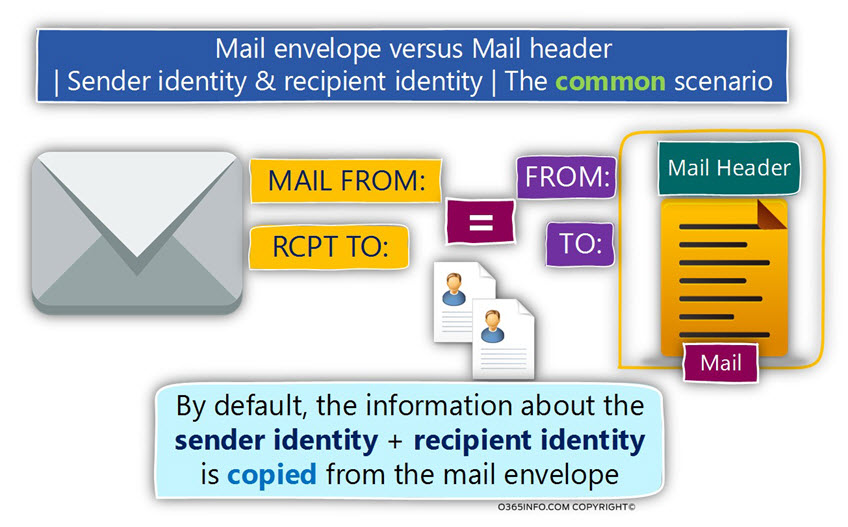
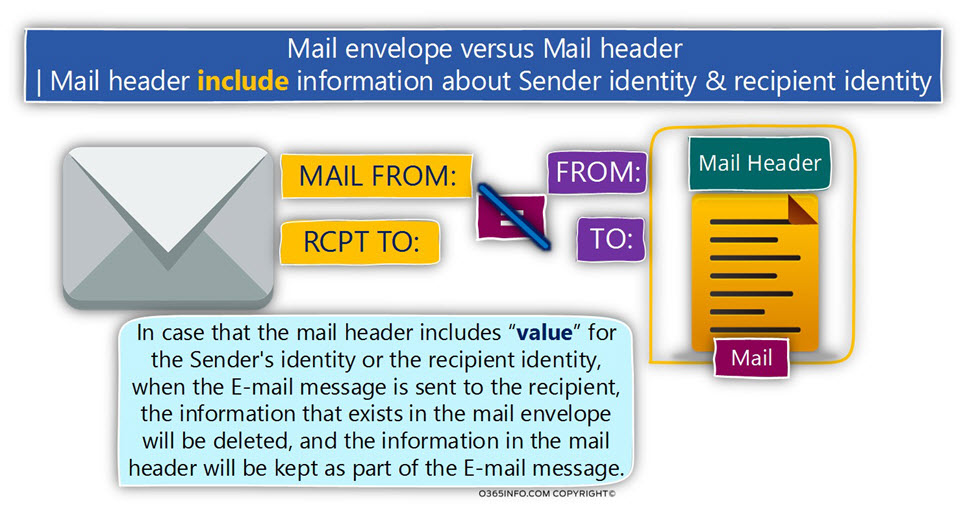
DKIM mail standard built on the Public key infrastructure
The DKIM standard is a mail security standard that enables us to implement a process, in which we can verify the identity of the sender + verify the data integrity of the content that’s included in the E-mail message.
The DKIM standard can provide these are capabilities by using methods and process from the world of Public key infrastructure.
The term “Public key infrastructure” is a very wide term that includes many different components, standard protocols, and algorithms.
The DKIM standard uses a very small fraction of Public key infrastructure that described
as Digital signature.
Regarding the subject of DKIM standard and Public key infrastructure, the main question that we can ask is:
Do we need to be familiar with Public key infrastructure in order to use the DKIM standard for protecting our mail infrastructure?
The straight answer is: “No”, especially in an Office 365 based environment that provide us a very easy and simple way for implementing the DKIM standard.
Although that the implementation of the DKIM standard in an Office 365 based environment can be activated in “one click”, my opinion is that we must understand quite well the subject of the Public key infrastructure and how does the DKIM standard uses this infrastructure.
The need to understand the “behind the scenes” of DKIM standard is because when we need to implement the DKIM standard in complex mail environment or, to a troubleshooting scenario in which the DKIM standard is involved, we must be equipped with broad knowledge about the Public key infrastructure and the specific characters of the DKIM standard and the Public key infrastructure features that he uses.
Most of the technical articles that include a description of the DKIM process assume that the reader is already familiar with the concept of Public key infrastructure, Digital signature, Certificate and so on.
However, in reality, most of us have a very superficial knowledge about Public key infrastructure.
When reading a technical article about DKIM standard that includes Public key infrastructure “buzz words”, the outcome is that we are left with a feeling frustration because we are not relay understand this “mambo jumbo” process.
The purpose of this article is to help you demystify the subject of Public key infrastructure and to provide better understanding regarding the way that DKIM standard uses the Public key infrastructure for implementing his main purpose – enable the receiver to verify the sender identity.
Q1: Do I have to read this information to be able to apply DKIM?
A1: No you don’t. If you want to know how to “activate” the DKIM signature for outgoing
E-mail in Office 365, you can jump to the article – How to enable outbound DKIM signing for your domain in Office 365 |Part 5#5
Q2: Does the Public key infrastructure is relevant only to DKIM infrastructure?
A2: No, the concept of – Public key infrastructure is used by many standards and protocols such as TLS, HTTPS and more.
Q3: Does the information that provided in the current article about the Public key infrastructure will help me to fully understand this infrastructure?
A3: No, in the current article, we will review only a fraction of the Public key infrastructure which relates to the process of Digital signature that serve as an essential component in the DKIM standard.
Q4: Does the description of “DKIM flow” in the current article, include all the specific details that involved in a standard DKIM flow?
A4: No, the current article will provide a high-level view description of the DKIM flow that doesn’t include an exact description of each detail that involved in the DKIM process \flow.
DKIM and the Public key infrastructure
The purpose of the DKIM standard is to enable both sides – sender and receiver, to use mail infrastructure in a secure manner.
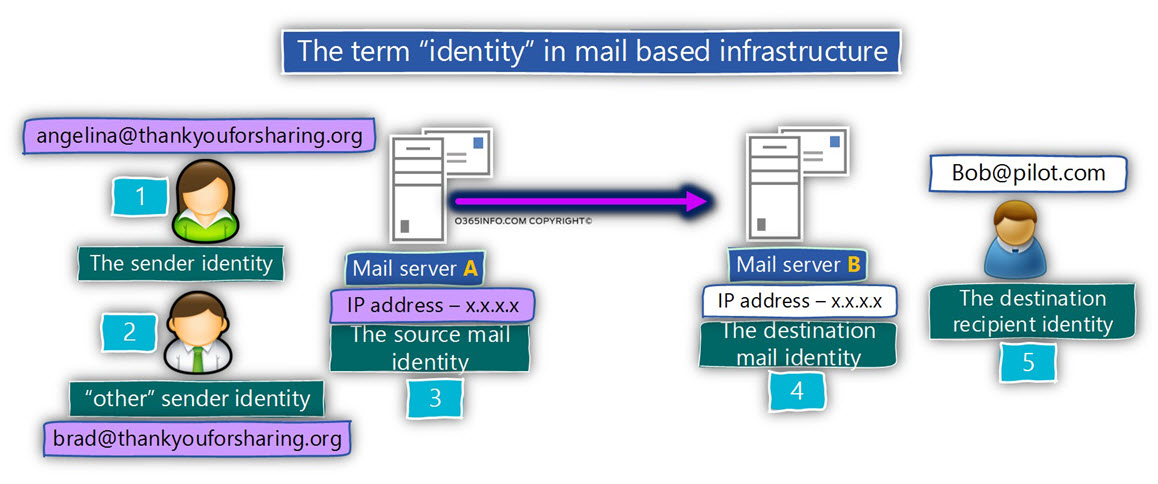
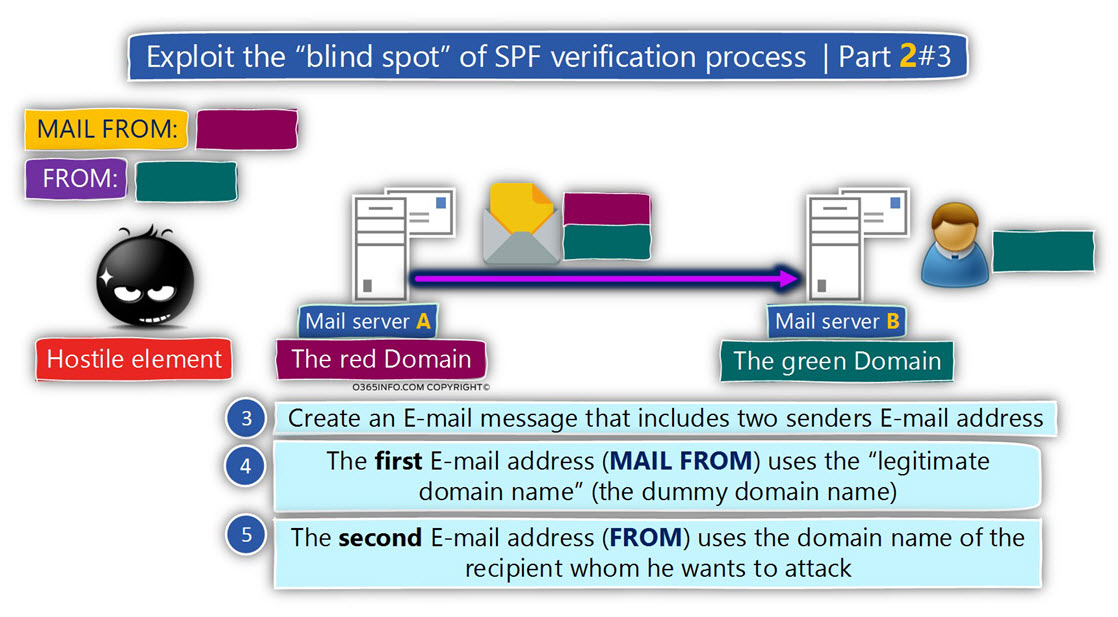
- The DKIM standard is used by the sender, as a tool for preventing a scenario, in which hostile elements will use his identity (his public domain name) when they attack “other organizations”.
- The DKIM standard is used by the receiver, as a tool for verifying the identity of the sender and by doing so, prevent a scenario in which hostile element will spoof or use a fake identity of a legitimate organization.
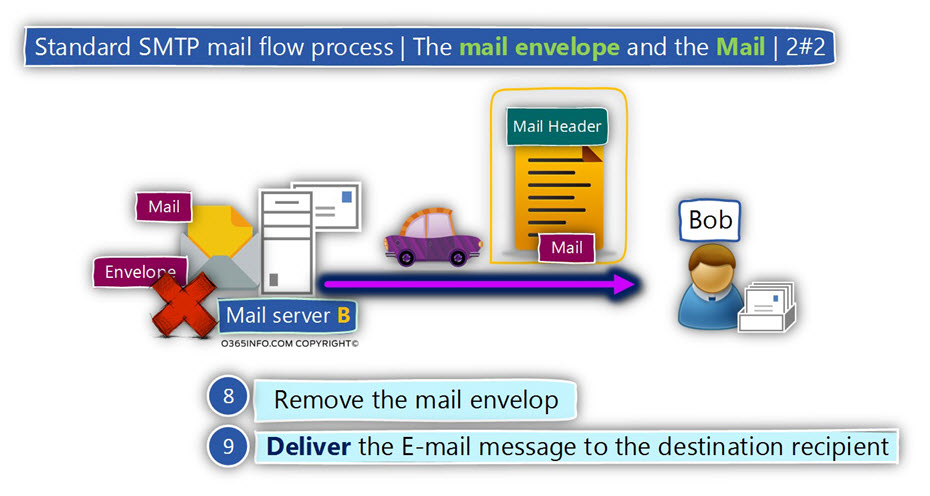
The DKIM standard enables the side that represents a specific mail domain to “stamp” his true identity into E-mail messages that leave his organization so, the “destination side”
(the receiver), will be able to verify if the E-mail message.
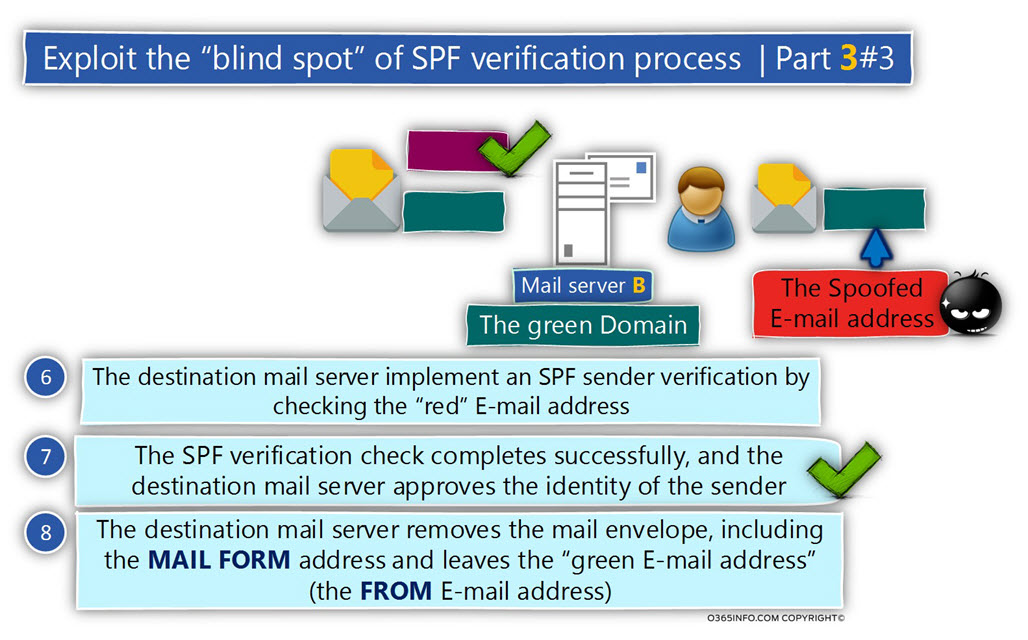
The receiver mail server will decide if the E-mail message was indeed sent by a trusted source or if the E-mail message was sent by a “sender” that his identity cannot be verified and for this reason, the E-mail item can be classified a suspicious or problematic.

Sender side
The main ways of the “sender side” meaning, the mail infrastructure that uses DKIM standard is – to “stamp” each E-mail message with a “unique sign”, that will prove his identity and let the destination recipient be sure that a specific E-mail message was sent by “him” (by the mail server that represents a specific E-mail domain name).
This goal is accomplished by – using a Digital signature process that will. Digitally sign each E-mail message that leaves the organization mail infrastructure.
The receiver side
The main ways of the “receiver side” meaning, the mail infrastructure that accepts the
E-mail message is:
- Know with certainty, that an E-mail message that uses an E-mail address with a specific domain name was sent from a legitimate mail server that represents the domain name.
- Know with certainty, that the information that appears in the E-mail message header was not altered in any way.
This goal is accomplished by a process in which the receiver side opens the E-mail message that includes the Digital signature and implements a process of verifying the Digital signature.

The main purposes of Public key infrastructure and how does DKIM uses Public key infrastructure
As mentioned, the information about the Public key infrastructure that will be provided in the next sections is just a small fraction of the “big picture” that describe the true meaning of Public key infrastructure.
One of the main problems (or if you would like to use the politically term – “challenge”) is the ability to describe a specific component of the Public key infrastructure, without using technical terms that relate to additional or parallel components of the Public key infrastructure.
In other words, to the task of describing the Public key infrastructure “from scratch” meaning begging with the description of” the first layer” and then move on to the “second layer”, is almost impossible because each of the different layers is interlaced with each other.
Bottom line
Be patient!
At the begging, the information looks messy and unclear, but down the road, as we continue to read the information things will get clearer.

In this article, our main goal is not to provide a detailed information about each of the
Public key infrastructure components but instead, focus on the specific Public key infrastructure components meaning Digital signature, which is used when implementing DKIM.
The purpose of using Public key infrastructure in general
Generally speaking, the purposes of Public key infrastructure are:
- Data encryption – the ability to transfer data over a non-secure channel in a way that only the two parties that are involved in the communication process will be able to read the data.
- Identification – the concept in which a specific side needs to prove his identity with absolute certainty to the other side.
- Data integrity – the ability to ensure that the data that was sent over the communication channel to the “other side” is the original data, meaning the data has not changed or altered.
The DKIM uses these “three Public-key infrastructure building blocks”: Encryption, Identification, and Data integrity for accomplishing the goals if enabling the sender side to digitally sign email messages and, to the receiving side – to verify the identity of the sender.

The concept of public key and private key pair
The term “key pair”, describe a set of the two encryption keys, that created based on a cryptographic algorithm.
One key described as Public key, and the second key described as Private key.

The “key pair” (the Public key and Private key) is mathematically linked.
The concept of using Public and Private encryption keys, describes as “Asymmetric cryptography” because, we use different keys for encrypting and decrypting the data.

Symmetric cryptography
Technically speaking, there is an additional encryption method in which we use “symmetric cryptography” meaning – we use only one key for encrypting the information and the same key for decrypting the information.
The common term for this key is – Session Key because, in Public key infrastructure, we use this key to encrypt data in a specific session of for a specific time period.
Public key infrastructure
The term “Public key infrastructure” was created for describing a very complex and sophisticated infrastructure that included many components that use the “Key pair” (the Public key and the Private key) for various operations.

General note regarding the term – “Public key infrastructure”.
Despite the fact that we use a combination of Public key and a Private key and despite the fact that the “security infrastructure” uses many other components such as CA (Certificate Authority), certificate, HASH algorithm, Digital signature, Symmetric key and much more, the common term that is used for describing an infrastructure that uses Public + Private keys is – Public key infrastructure.
The purpose of Public-Private key
A reasonable (but wrong) assumption is that we use two sets of keys because, one of the keys was created for encrypting data and the other key, was created for decrypting
(remove the encryption) data.
The reality is a little complicated because the mathematical formula that we use for creating the special set of “keys”, provide each of the keys the ability to encrypt data and also decrypt data that was encrypted.
Each of the keys has a unique character:
- The Public key as the name implies, is known to everyone.
- The Private key is a “Secret Key” that is known only to the owner of the key pair.
The Private key should be kept in a secure manner and be accessible only for the “owner” of the key pair.
Versus this concept, the Public key should be published so, everyone will have access to
the Public key and the ability to read the value of the Public key.

As mentioned, booth of the keys (the Public Key and the Public Key) used for Encrypting data + Decrypting data.
When using a Public key infrastructure, the following rules are applied:
- Data that was encrypted using the Public key can be decrypted only by using the Private key.
- Data that was encrypted using the Private key can be decrypted only by using the Public key.

In a Public key infrastructure, we use the Key pair in the following manner:
The use of Public Key
1. Encrypting data
Most of the time, we use the Public Key for encrypting a very specific data – the information about the Session key.
In a scenario in which we need to encrypt data that travel over a non-secure infrastructure between two parties, in a Public key infrastructure, we use a Session key for encrypting the data (in also for decrypting the encrypted data).
We will not get into the specific detail, but in general, the process of decrypting data by
using Public key is very resource intensive.
For this reason, we use the Public key as a “one-time process” for encryption the Session key that will be used for a specific session between the two parties that are involved in the communication channel (using the Session key is fewer resources intensive).

2. Decrypting information
In a Public key infrastructure, we use the Public key also for decrypting information meaning, remove the encryption from a specific data.
When using the option of Digital signature, the receiver, uses the Public key of the sender for decrypting the HASH value that appears in the Digital signature.

The use of private key
1. Encrypting information
When the sender needs to create a Digital signature, he uses the Private key for encrypting the HASH value that included in the Digital signature.

2. Decrypting information
In a Public key infrastructure, we use the Private key for decrypting data.
In a standard communication channel that uses the Public key infrastructure, one of the sides such as side B generates a Session key (encryption key that is used only for a specific session or for a limited amount of time) and encrypt the Session key by using the public key of side A.
When side A get the data (the encrypted Session key), side A will remove the encryption using his Private key.

The use of the term “Encryption” in Public key infrastructure
In this section, I would like to review the term “Encryption” when relating to
a Public key infrastructure.
The process “Encryption” can be implemented by using a:
- Public key
- Private key
- Session key
In addition, the use of “Encryption” that is implemented in Public key infrastructure, can be classified into two major scenarios:
- Data encryption – using the encryption process for encrypting data that flows through the channel of communication between the two entities involved.
- Digital signature – encrypting the HASH value that included as part of a Digital signature.
The DKIM standard uses encryption only for the purpose of Digital signature.
When using a Digital signature, we don’t wish to transfer data in a secure manner (by encrypting the data) but instead, implement a concept which enables side B to identify and trust the identity of side A.
In the following diagram, we can see that the DKIM standard doesn’t need the “encryption type” that is used in a Public key infrastructure, for delivering data over a non-secure communication link (encrypting the data himself).
The DKIM standard uses only the “second form of encryption”, in which the encryption option is used for encrypting the HASH value.

Public key infrastructure | Data encryption | Type 1#2
In the following section, we will review the process of encrypting data that which is transferred through a communication channel between two parties.
As mentioned, this type of data encryption” is not implemented when using DKIM.
Although this part is not directly related to the DKIM implementation, it’s important that we will have general knowledge of this “Public key infrastructure part”.
In a Public key infrastructure, the data encryption process is implemented in the following way:
Side A and side B want to secure data that passes through a non-secure communication channel (such as public network, etc.).
To accomplish this goal, the following conditions must be met:
- Side A and side B will have to agree on a specific method (encryption key) that will be used for encrypting and decrypting the data which is transferred via the communication channel.
- Side A and side B will have to agree on a method that will enable them to share the encryption key.
- Each of the involved parties (side A or side B) that send data to the “other side”, will use the key for encrypting the data.
- Each of the involved parties (side A or side B) that get data from the “other side”, will use the key for decrypting the data.
Data encryption key.
In a Public key infrastructure, we use the same key for encrypting the data and also for decrypting the data.
The side that generates the session key.
One of the involved parties (side A or side B) is responsible for generating the “key” that’s described as Session key.
Deliver the session key in a secure manner.
This is the part which enables the involved parties (side A or side B) to share the Secret key so the side that generate the Session key (side B in our example) will be able to deliver the secret key to the “other side” over a non-secure infrastructure.
The side that generates the Session key (in our example side B), will use the Public key of side A for encrypting the “Secret Key” (the Session key) that will be used by both involved parties (side A or side B).
Note – in reality, the scenario is more complicated because we need to find a way to enable each of the sides (side A and side B in our scenario) to verify the identity of each other, before the phase in which the sides exchange the information about the Session key.
Step 1#4
- Side B generates a Session key (Secret Key).
- Side B encrypts the Session key with the Public Key of side A.
- Side B sends the encrypted data to side A.

Step 2#4
- Side A get the encrypted data.
- Side A uses his Private key for decrypting the data. In this phase the term “data” realities to the value of the Session key.

Step 3#4
When side A need to deliver data to side B, side A will perform that following steps:
- Side A uses the Session key (the Session key that he got from the former phase) for encrypting the required data that he needs to send to side B.
- Side A sends the encrypted data over the communication channel to the “other side”.

Step 4#4
- Side B gets the encrypted data.
- Side B will use the Session key for decrypting the data

Public key infrastructure | Digital signature | Type 2#2
An additional implementation of the term “Encryption” in Public key infrastructure is implemented when using Digital signature.
When side A creates a Digital signature, side A encrypts the HASH value using his Private key and the receiver (side B) use the Public key of side A for decrypting the information.
As mentioned before, the DKIM standard uses Encryption only for implementing Digital signature.
In the current article, we will mention the term “Encryption” many times.
In the context of this article, we use the term “Encryption” for describing the process which is implemented when using Digital signature.
The concept of HASH
In DKIM implementation, the sender (the mail server that represents the sender) uses a Digital signature that is attached to the E-mail message.
The purpose of this “Digital signature” is to enable the receiver (the mail server that represents the destination recipient) to implement a verification process in which he verifies the identity of the source recipient (the sender).
The Digital signature that the sender creates, is implemented by using the following steps:
- Use a HASH function to collocate the HASH value of a specific E-mail header.
- Get the HASH result.
- Encrypting the HASH value using a Private key.
The question that can appear in our mind is: what is this “HASH” thing?
In this section, our main focus is to try to understand better the concept of “HASH“.
The term “HASH” defines is a mathematical function, that we use for processing a specific data and the outcome describes as HASH value or Message Digest.
The HASH value (the result) totally depends on the value of the “original data”.
Even if one bit of the “original data” is changed, in case that try to use again the HASH Function, the outcome meaning, the HASH value is totally different.
The Ingredients of the HASH process are as follows:
1. The original data.
The is the text or the “source” that we want to HASH by using a HASH function. The “source” could be a single word or a text that includes hundreds of thousands or even millions of characters.
2. The HASH function.
The HASH function is a mathematical formula that uses for generating the HASH value.

3. HASH value or a Message Digest
When we “feed” the HASH function with the specific data source, the HASH function will
“Grind” the data and describe the outcome as the HASH value or a Message Digest.

One of the most interesting things about the HASH function is that the result, meaning the HASH value (the Message Digest value) is a fixed value.
In other words – the HASH value length is not realities in any way to the “length” (number of or characters) of the original text on which the HASH function was used.

HASH function flow
In the following diagram, we can see the flow of the HASH function.
We take some text and “stuff it” to the HASH function “grinder”.
The HASH function “grinder” process, the data and the result are the HASH value that has a fixed length.
The “fix length” of the HASH value depends on the “type” of HASH function (HASH algorithm) that we use.
For example:
- A HASH algorithm named- SHA-1, produces a 160-bit (20-byte) hash value.
- A HASH algorithm named- MD5, produces a 128-bit (16-byte) hash value.

The HASH value
The HASH value that is produced by the HASH function is a very specific and unique value that “represent” the specific data\text that was “HASHED” by the HASH function.
In case that we make a very small change to the original data, such as – adding a space, comma or a period to the “source text”, if we use the HASH function again on the
“apparently same text”, the result will be totally different meaning the HASH value will be totally different.
Notice that the “length” of the HASH value will stay the same, but the HASH result will be a totally different result.

HASH function and the “non-reversible concept”.
Another important concept of the HASH function could be described as “non-reversible concept”.
The meaning of this concept is:
in case that we have in our possession the HASH value, we can never use a process such as a “reverse engineering”, in which we generate the original data from the HASH value.
In other words – the HASH value could not be used in any way by any element in getting the “original data” that was hatched by the HASH function.
We can use a not very nice metaphor to demonstrate the concept of “non-reversible”:

The real purpose of using the HASH process
The main purpose of the HASH process is not to encrypt a specific data, but instead, provide us a mechanism, which we can use for verifying the integrity of the data.
For example – when we get a specific message, to be able to be sure that the message content that reaches to us is the “original content”, that was created by the sender. In other words, to be able to be sure that the message content was not altered or change in any way.
As mentioned, the HASH vale considers as “no reversible” meaning we cannot use the HASH value for “generating the original data.
In other words, side B cannot use the HASH value that sent from side A for “revealing” the original data that was sent.
Instead, the way that we use the HASH procedure is by comparing the “original HASH value” to a “computed HASH value” that is generated by the receiver (side B).
The process that we use for verifying the Data integrity of the message content, that sent to us, is by implementing a procedure in which the destination side (the receiver or side B in our example)
Take the text that was sent by the sender
- Uses the same HASH function (the same HASH algorithm) on the “source data”.
- “Write down” the HASH value.
- Compare the HASH value that he got to the original HASH value that is included in the message that sent from side A.
In case that the “computed HASH value” is identical to the “original HASH value,” we can assume that the data was not altered or change in any way.
In the following diagram, we can see the concept in which booth on the side (the sender and the receiver) will need to use the HASH function for computing the HASH value of a specific “block of text”.

In the following diagram, we can see the concept in which side B (the receiver) needs to compare the two different HASH values:
- The “original HASH value” that was computed by side A and sent as part of the
E-mail message. - The “HASH value” that was computed by side B.

In case that the booth of the HASH value is equal – the meaning is that the data that he got is the original data (the data hasn’t changed or altered in any way).
The identity of the sender who sends the data
The use of HASH enables us to be trusted the “data integrity” meaning to be sure that the original data that was created by the “sender” was not altered.
But one important question that was not asked, up until now, is – how can we trust the “sender”?
How do we know that the sender is really who he claims to be?
In a Public key infrastructure, the answer for this “need” is implemented by using a Digital signature.
The Digital signature enables the sender to prove his identity to the receiver by encrypting the
HASH value that he sends using his private key.
Additional reading
Digital signature
Digital signature is a major component in Public key infrastructure.
Using a Digital signature, enables us to fulfill two major security needs:
- Data integrity
- Proof of identity

In the former section, we have to review the subject of “HASH” and learn how we can use the “HASH Process” for verifying the integrity of a specific data that sent to us.
In addition, we show that the “HASH process” doesn’t provide a way for enabling us to verify the identity of the sender.
In Public key infrastructure, the “tool” that we use for using a mechanism which enables us to verify the identity of a specific sender is by implementing a process which includes the following steps
- Side A (the sender) encrypt a specific “piece of data” using his Private key.
- Side A (the sender) send a message that includes the encrypted piece of data to the other side (side B).
- Side B (the receiver) tries to decrypt the encrypted piece of data by using the Public key of side A.
- In case that he manage to “crack” the encryption by using the Public key of side A, this is a Definite proof beyond doubt that the message was indeed sent by a legitimate sender (side A) because only the sender who has access to the Private key could have to encrypt the specific data in a way that could be decrypted by using the Public key.
In our scenario, the “piece of data” is the HASH value that is generated and attached to the E-mail message by side A.
In a Public key infrastructure, the combination of – HASH value that is encrypted by a privet key described as Digital signature.

Generally speaking, the “trust concept” could be realized as:
- Two-way trust – side A need to be able to trust side B and vice versa.
- One-way trust – side B needs to be able to trust sides against A but not the opposite meaning side A doesn’t need to trust side B.
In a Public key infrastructure, the process of Digital signature is implemented most of the time as a One-way trust.
In other words, most of the time one of the sides such as side A need to be able to proof his identity to side against B so, side B could trust him,
This doesn’t mean that side B in our example should also proof his identity to the side A.
In the following diagram, we can see the concept of data that was encrypted by suing a Private key. Only the “real sender” meaning, the owner of the Private key has access to this key!

An example of using Digital signature in DKIM session
In the following section, we will review scenario that is implemented when using the DKIM standard in mail based environment.
In our scenario, recipient A wants to send an E-mail message to the recipient B.
To be able, the mail infrastructure that represents recipient B to trust the identity of recipient A, the mail server of recipient A will use DKIM for a digital sign the E-mail message.
When the E-mail message reaches to the mail server that represents recipient B, the mail server will verify if the “DKIM signature” is valid.
in case that the signature is valid, the mail server will forward the E-mail message to the recipient B.

Our goal
The main goal is to use a method, in which the hosts who will get the E-mail message that sent from side A, will be able to be certain beyond doubt that the message was sent by side A and the information were not altered or changed in any way.
Given that bout of the involved parties supports DKIM standard, the DKIM flow between the two of the sides will be implemented in the following way:
- Side A uses a HASH function to HASH specific “piece of data”. In DKIM scenario, this “piece of data” relates to E-mail data fields such as – the sender E-mail message, the destination recipient E-mail address, the E-mail message subject and more.
- The result is a HASH value.

- Side A add to uses his Private Key for encrypting the HASH value.

- The result is a Digital signature.
- Side A “attached” the Digital signature to the E-mail message and send the information to the other side.

Side B gets the message. Side B has two main goals:
- To be able to know that the message was indeed sent by the recipient A.
- To be able to know that the information in the E-mail message is the “original information” meaning, the information was not altered or changed in any way.
To be able to accomplish these goals, side B (the mail server that represents recipient B) will implement two different actions:
- Side B gets the E-mail message.

- Side B gets the E-mail message and read the DKIM header that includes the host name of the TXT record that includes the public key of side A.
- Side B will fetch the value of the Public Key by addressing DNS server and ask for information about the specific record.

- Side B tries to decrypt (remove the encryption) of the HASH value in the message using the Public Key that he got from the former step.
- In case that side B manage to complete the decryption process, side B can be certain beyond doubt, that the “originator of the message” is side A because, only the side A Public Key could have been open from the encrypted “piece of data” (the HASH value).

- Side B will collocate the HASH value of specific E-mail fields that appear in the
E-mail message. - Side B will “write down” the HASH value because later on, side B will perform a comparison of the HASH value that he got from the calculations.

- Side B will perform a comparison process in which he compares the HASH value that he got from the calculations to the HASH value that appear in the E-mail message the was sent from side A.
- In case that the HASH value that was calculated is equal to the HASH value that appears in the E-mail message, the meaning is that the mandatory requirement of Data integrity was fulfilled.
Side B (the mail server that represents recipient B) approve that the DKIM signature is a valid signature meaning – he trusts the identity of the sender (recipient A).

The next article in the current article series
In the next article – DKIM flow in Office 365 | Part 3#5, We will take a peek behind the curtain of the events that occurs in a standard DKIM flow.
We really want to know what you think about the article
The post DKIM as standard that based upon the Public key infrastructure | Part 2#5 appeared first on o365info.com.