The implementation of Hybrid configuration in Office 365 could be considered as a simple task or exhausting process. The experience that we will have is depend on the “readiness level” of the Exchange On-Premise and other related components.
In simple words: in case that you understand what are the pre requirements that need to be configured and implemented, before starting the Hybrid configuration wizard, most of the chances that running the HCW (Hybrid configuration wizard) we be an easy task and, the process will complete successfully. In this article, we will review:
- The pre requirement of Exchange hybrid environment
- Best practices and recommendation for the required preparations
- Tools and methods that will help us to check and verify if the on-Premises environment was configured correctly.
Toc | Pre requirement of Exchange hybrid environment
Part 1:Hybrid deployment in Office 365 | Checklist and pre requirements | Part 1/3
Part 2:Hybrid deployment in Office 365 | Checklist and pre requirements | Part 2/3
To be able to optimize the navigation in the article, you can use the collapse and expand option.
| Collapse All Headers |
Hybrid configuration in a Nutshell
The term Hybrid configuration or Hybrid environment, describe a scenario in which two separated Exchange organizations that belong to different Active Directory forests are working as a “one unit” The term Hybrid configuration was created, for describing this type of relationship between the Exchange On-Premise infrastructure and the cloud (Exchange Online) infrastructure.
For example, in the following diagram, we see the logical concept of Hybrid environment. The Public domain name: o365info.com, configured as a “shared domain”. The meaning is that two separated Exchange infrastructure “represent” this domain name or shared between them the same domain name.
When looking at the diagram, we can see two recipients: Bob@o365info.com and Alice@o365info.com
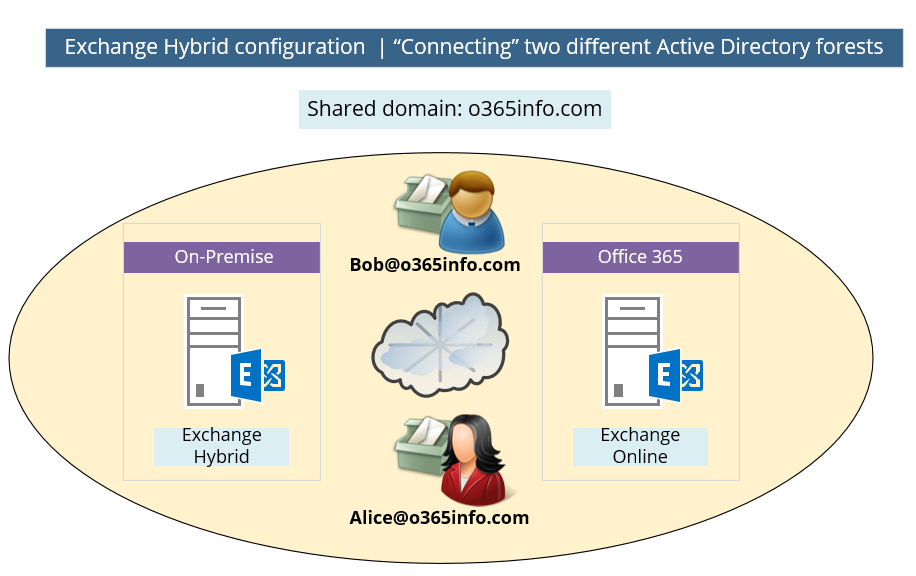
Technically, the recipient mailboxes must be configured on the Exchange on-Premises server or at the Exchange Online server, but logically, Bob and Alice don’t know where their mailboxes hosted.
In case that Bob mailbox is hosted on the Exchange on-Premises server and Alice’s mailbox is hosted on an Exchange Online server, Bob and Alice will have all the standard Exchange services such as: Free\Busy time, mail tips and more as if they are hosted in the same Exchange organization because, the Hybrid environment “connect” the two separated Exchange environments and making them appear as one entity.
Hybrid configuration relationships and Trust concept
As mentioned before, the Hybrid configuration was designed for “connecting” two different Exchange environments and make them operate as one entity. The “glow” between the two separated environments is implemented by a trust concept.
- Federation trust – each of the Exchange environments (on-Premises + cloud) needs or must trust a thread element named: MFG – Microsoft’s federation gateway (number 1 in the diagram).
- Exchange organization relationships – a trust model between two separated Exchange organizations. In Hybrid environment, the Exchange organization relationship is implemented between the Exchange on-Premises forest and the “Office 365 forest” (Exchange Online) (number 2 in the diagram).
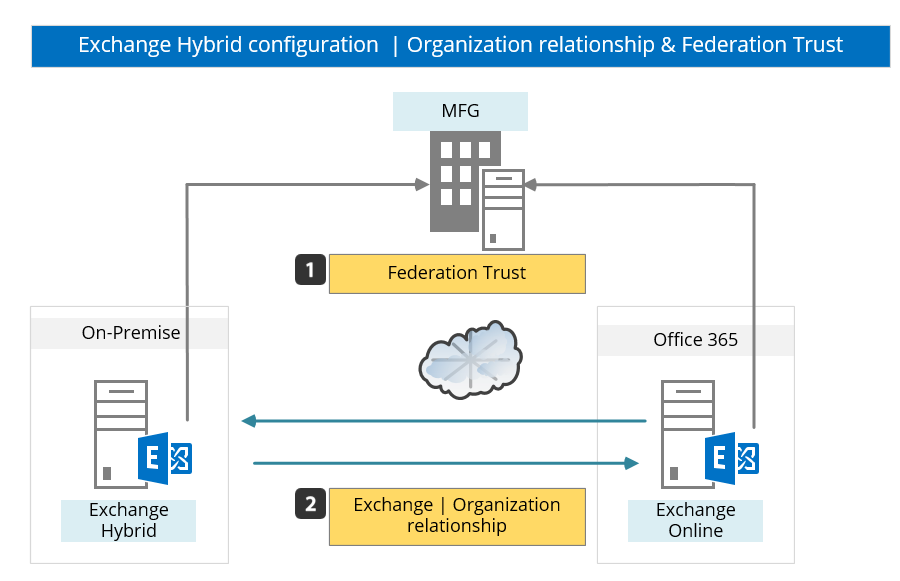
The Hybrid configuration and the “Trust model” enable each of the “end points” (Exchange on-Premises and Exchange Online) to:
- Authenticate each other
- Verify the identity of each other
- Create a secure communication channel: Encrypt the information and implement data integrity by using a public certificate and by using a secure communication protocol such as: SMTP\TLS and HTTPS.
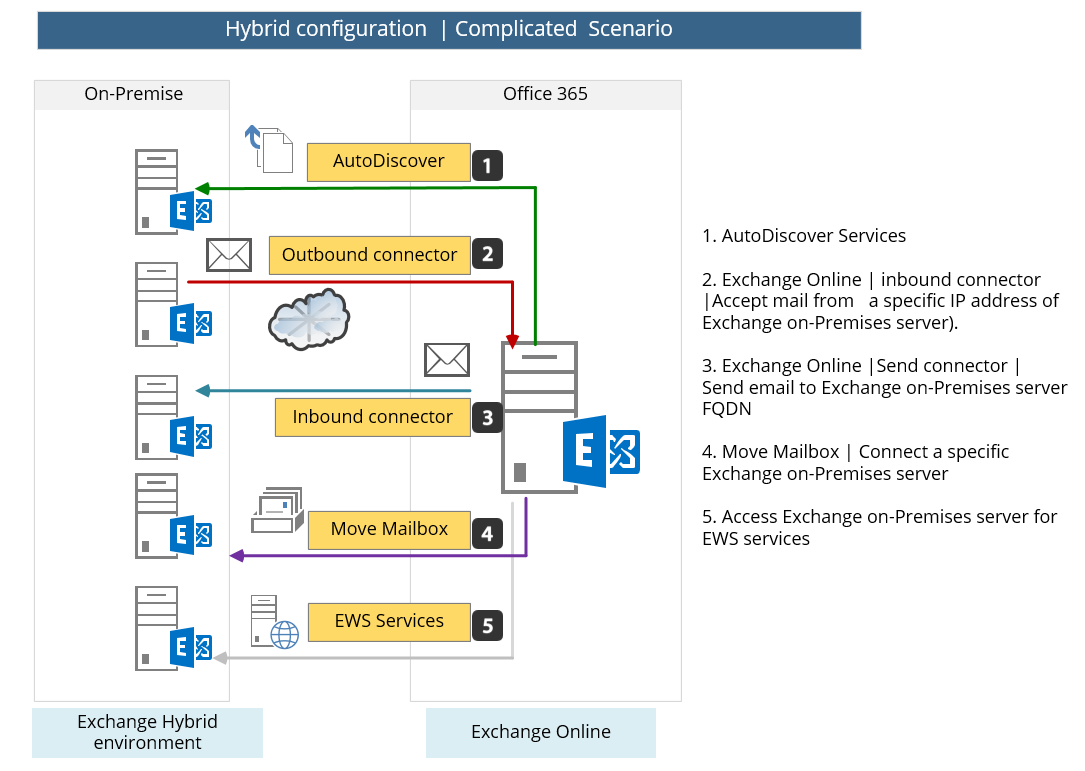
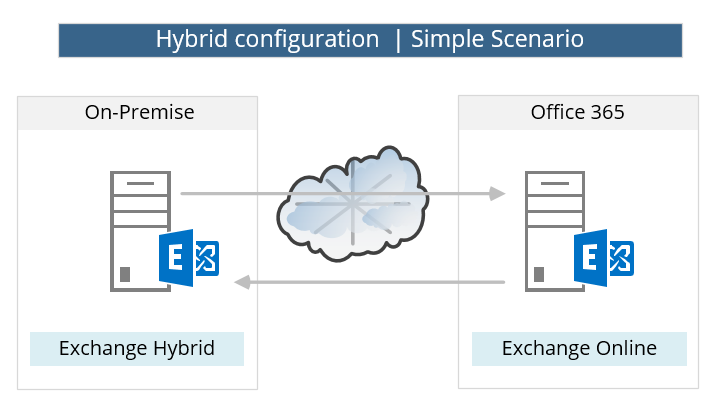
Simple Exchange on-Premises environment verses complicated environment.
The term “Hybrid configuration” could use in describing a very simple scenario in which the organization has only one Exchange on-Premises server, who serves as a Hybrid server and is responsible for creating the “communication channel” between the on-Premises environment and the “cloud” (Exchange Online).
Another scenario of Hybrid configuration could be a more complicated scenario, which is more common in enterprise environments that have complicated Exchange on-Premises infrastructure.
In this scenario, the “relationship” between the Exchange Online and the “on-Premises Exchange infrastructure” could be divided to many “communication channels” with different\separated Exchange on-Premises servers.
For example: the mail flow between Exchange on-Premises and Exchange Online could be implemented by using a “dedicated” Exchange on-Premises server who will be configured for sending mail to Exchange Online and, other Exchange on-Premises server who will be configured to “accept” mail from Exchange Online.
Another Exchange on-Premises server could be assigned for different roles\services such as: dedicated Exchange on-Premises server who will provide AutoDiscover services, dedicated Exchange on-Premises server who will provide EWS services and so on.
Pre requirement for Hybrid deployment in Office 365
In the next sections, we will review each of the components that includes in the “Pre requirement for Hybrid environment list”
1.Exchange Hybrid server version
The term “Exchange Hybrid server” is just a logical term that describes Microsoft Exchange server who has the ability to be a part of a Hybrid environment.
The Exchange on-Premises server “Hybrid server” could be implemented by using:
- Exchange 2010 SP3
- Exchange 2013
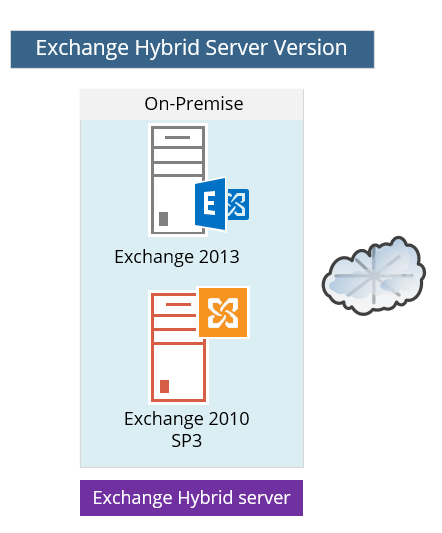
Exchange 2010 SP3 as Hybrid server
In case that we want to use an Exchange 2010 as a Hybrid server, the minimum requirement is service pack 3. Besides of the requirement for Service pack 3, the best practice is: to install the most updated Exchange Rollup versions because, each of the software updates (Exchange Rollup) includes solution to issues\problem that was discovered and the fixed is included in the Rollups.
Many times the customer or the organization IT will “resist” to the recommendation of “installing the most update Exchange rollup“ but, it’s important to emphasize that installing the most updates Rollups can prevent many of the future problems and consider as a major factor in the process of building the Hybrid environment.
The following quotation relate to Rollups 4 for Exchange 2010 SP3, but you get the idea.
[Source of information: Understanding Hybrid Servers in Exchange 2010 Hybrid Deployments ]Additionally, we recommend installing future Update Rollups 4 for Exchange 2010 SP3 on all your hybrid servers. Microsoft releases update rollup packages approximately every six to eight weeks. The rollup packages are available via Microsoft Update and the Microsoft Download Center. In the Search box on the Microsoft Download Center, type “Exchange 2010 SP3 updates rollup” to find links to the rollup packages for Exchange 2010 SP3.
Download link for the required Exchange on-Premises server software updates
Exchange On-Premise 2010 – Download Rollup
At the current time the most updated Rollup for Exchange 2010 SP3 is: Rollup 6
Update Rollup 6 for Exchange Server 2010 Service Pack 2 (KB2746164)
Exchange 2013 – Download Service Pack 1
Microsoft Exchange Server 2013 Service Pack 1 (SP1)
Exchange 2010 | How can I know what is the current Exchange Rollup?
In case that you want to get information about the existing status of the Exchange 2010 on-Premises server, you can view the current version by using the Help menu and click on the About Exchange server 2010.

In the following screenshot, we can see that the Exchange on-Premises server version is: 14.03.0.195.001

So the next question could be: how can I know what is the Exchange on-Premises server service pack or rollup version based on this number? To be able to “translate” the value to a clearer information, we can use the article: Exchange Server and Update Rollups Build Numbers
In the following screenshot we can see that the version number: 14.03.0.195.001 is “telling” us that the Exchange 2010 on-Premises server includes an installation of Service pack 3 + Rollup 6 for Exchange 2010 SP3.
New Hybrid server versus existing Exchange On-Premise
In case that the organization Exchange infrastructure is based on older versions of Exchange such as: Exchange 2003, 2007, we will need to “add” or install a new Exchange on-Premises server (2010 SP3 or 2013) that will serve as the “Hybrid server”.
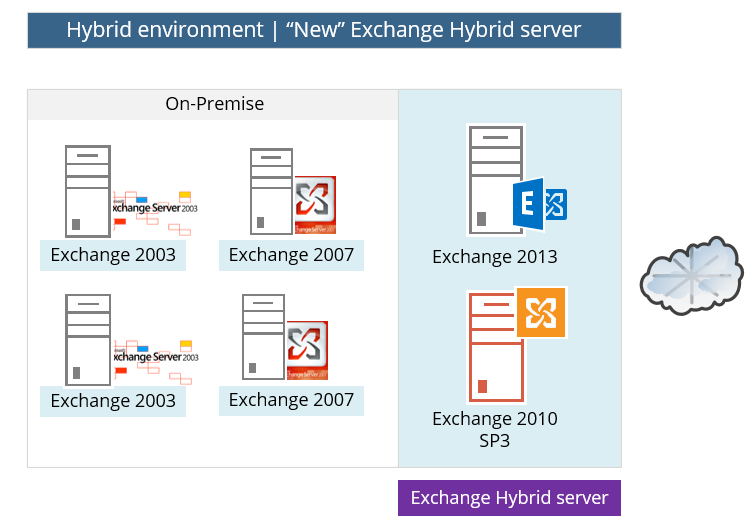
The “New” Exchange On-Premise Hybrid server could be implemented as Exchange 2010 or Exchange 2013 but, the best practice is to install Exchange 2013 server instead Exchange 2010 because: Exchange 2013 includes to improve features that relate to the Hybrid environment.
You can read more information about the improvement in Exchange On-Premise 2013 in the following articles:
2. Exchange On-Premise Hybrid server | Public IP address and Public name (FQDN)
Hybrid configuration is all about enabling Exchange On-Premise server who is configured as “Hybrid server” to create a communication channel with the Exchange Online infrastructure that exists in a public network.
To be able to communicate hosts or “endpoint” from a Public network, the Exchange Hybrid server must have:
- Public Name – The public name of the Exchange Hybrid server should be published in the Public DNS and should be resolved to the Public IP of the Exchange Hybrid server.
- Public IP address – A Public IP address that “Point” to the Exchange Hybrid server should be assigned. Most of the time, the Public IP address will not directly be assigned to the Exchange on-Premises server, but instead, the Public IP will be assigned to a Firewall server who will accept the communication requests to the Exchange on-Premises server and forward the request to the internal IP address of the Exchange on-Premises server.
For example, in case that the Outbound mail flow is based on two Exchange on-Premises servers who can send mail to the Exchange Online server, each of this server will need to have a dedicated Public IP address.
How can I know what is the Public name of the Exchange On-Premise?
The simple answer is that if you are the Exchange On-Premise administrator, you supposed to know what the Exchange On-Premise public name is but, in some scenarios, we will have to configure and hybrid deployment in an environment which we are not familiar with.
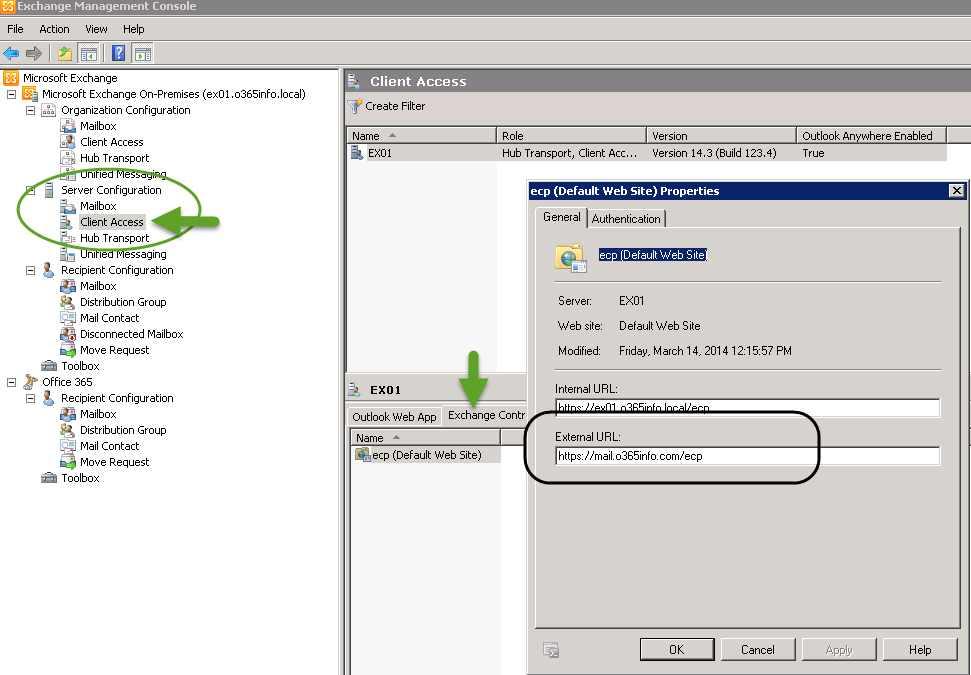
One option to get information about the “Public name” of the Exchange On-Premise server is by looking at the “External URL” that appears in the “client access” section under server configuration in the Exchange MMC (when we use Exchange 2010 MMC).
In the following example, we will look under the “Server configuration\Client access\EX01”
Exchange server “publish” couple of services. In our example, we look under the ECP tab (the ECP tab includes the internal + External URL of the Exchange server for using the web management interface).
We can see that the “pubic name” (External URL) of the Exchange On-Premise is: mail.o365info.com
Verify that the Exchange Hybrid server Public name (FQDN) is mapped to his Public IP
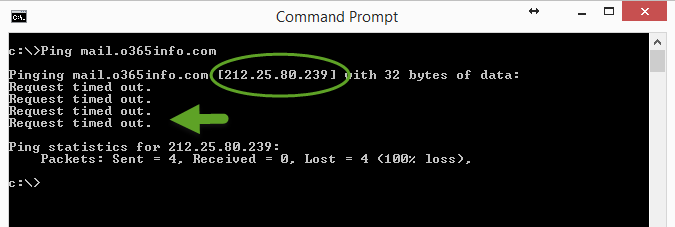
The verification process of the Exchange On-Premise Public IP is very simple. Open the command prompt and Ping the Public name of the Exchange On-Premise server. In our example, the Exchange On-Premise public name is: mail.o365info.com
In the following screenshot, we can see that we got as an “answer” the public IP of the Exchange On-Premise server.
One of the most common misconceptions is – that there is a problem because we got a “Request timed out”.
This response is not a sign of a problem because, the host whom we “ping” (Exchange On-Premise in our scenario), was not supposed to reply to the ping request. This is a foreseeable result because, most of the time the organization Firewall blocks the ICMP protocol (that is used for the Ping reply).
To recap: the fact that we got as a response the Public IP is the required results, meaning the Exchange on-Premises server have a public name + Public IP address.
3. Exchange On-Premise Hybrid server | Port number and protocols
Hybrid configuration is based on sharing data and services between Exchange Online and Exchange on-Premises server. The communication channel is implemented by using two communications protocols:
- HTTPS – access to the Exchange services (from Exchange on-Premises server to Exchange Online and vice versa) is implemented by using the HTTPS protocol.
- SMTP – the SMTP protocol is used for implementing mail flow, and the data is encrypted using TLS (TLS over SMTP).
The basic assumption is that the Exchange on-Premises server is protected by a Firewall. To be able to successfully implement the communication channel, between the Exchange on-Premises server and the Exchange Online, we will need to verify that the Firewall includes the following inbound and outbound rules:
- Inbound rule that enables to access the Exchange on-Premises server using port 25 (SMTP) and 443 (HTTPS).
- Outbound rule that enables the Exchange on-Premises server to access Exchange Online using the port 25 (SMTP) and 443 (HTTPS).
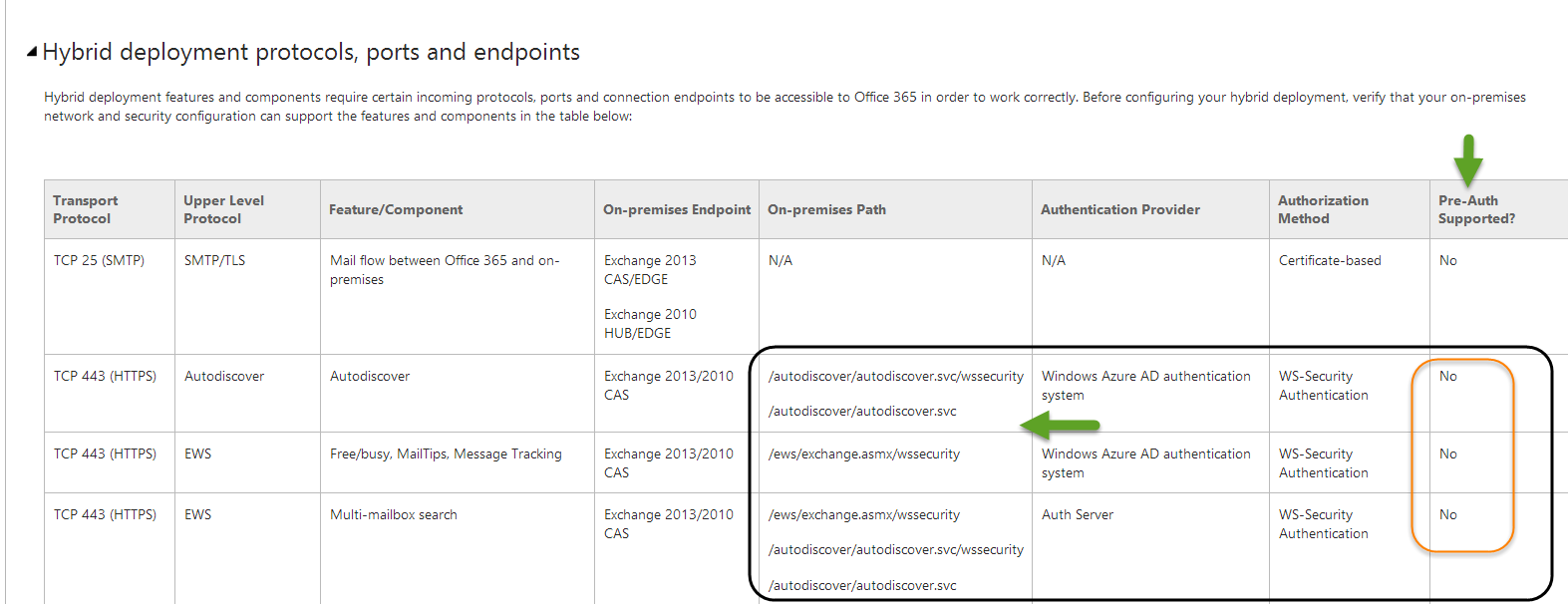
Reference from Microsoft article
The following screenshot is taken from a public Microsoft article and include a table the describe the port number and the services that need to be enabled for Hybrid configuration
Verify access from the public network to the Exchange Hybrid server
To verify that the required rule has been configured on the organization Firewall and, the Exchange on-Premises server can be accessed from the public network, we can use the option of “online scanning”.
There are many web sites that offer these services. Personally, I love to use the mxtoolbox web site. In the next step, we use the mxtoolbox for check what are the available ports on the Exchange on-Premises server.
In our scenario, the Exchange on-Premises server name is: mail.o365info.com
To get all the available options, we will choose the more menu and then the scan option.

We will provide the host name (or the IP address) of the host that we want to scan.
In the following screenshot we can see that the scan result show that the host mail.o365info.com is “listening” on port: 25 and 443.
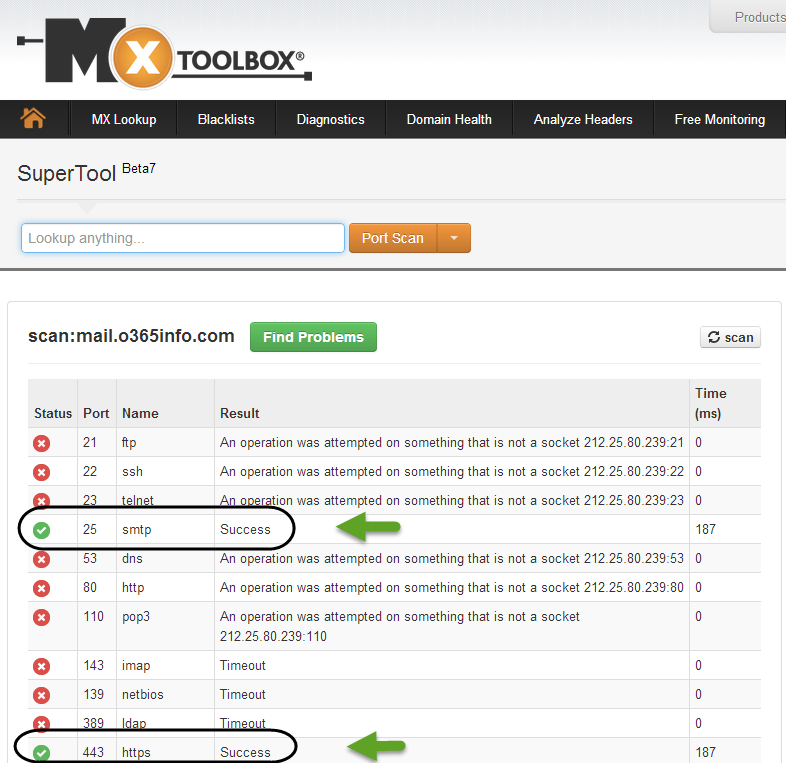
Verify that the Exchange Hybrid server, can access external network using the required ports.
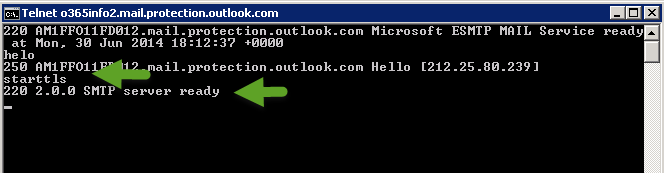
To be able to verify that the Exchange on-Premises server has access to public hosts using the SMTP (Port 25) protocol and can initialize a TLS session, we can use the Telnet command from the Exchange on-Premises server command prompt.
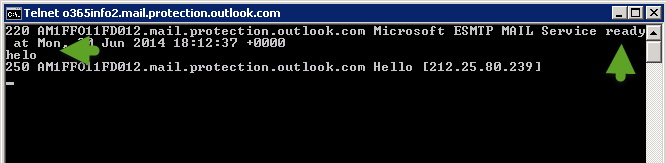
In the following example, we Telnet an external mail server using port 25 (Telnet o365info2.mail.protection.outlook.com 25)

We can see that the destination server “reply” and we get a response that the destination server is ready.
To start the SMTP\TLS session, we will type the command: helo, and after we get the “response” from the destination server, we can type the command: starttls
In the following screenshot we can see that the destination mail server reply with the message: “220 2.0.0 SMTP server ready”
4. Exchange On-Premise Hybrid server| Public IP address and Static NAT
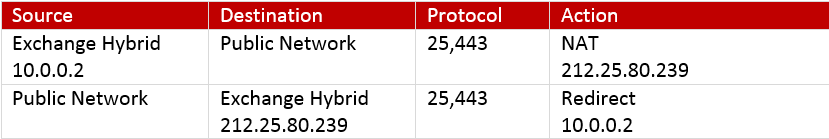
An important factor that we need to verify is that the Exchange on-Premises server is using the public IP address that was assigned to him when he responds to a communication request of external hosts or when he initializes a communication to an external host.
The technical term for this scenario could be as a “two way static NAT”.
For example: when using the Exchange 2010 Hybrid configuration wizard, we need to provide the public IP of the Exchange on-Premises server who is “allowed” to send email to the Exchange Online server.
When the Exchange on-Premises server will communicate the Exchange Online, it’s important that the Exchange on-Premises server will be represented by the public IP that was configured in the wizard.
Other examples could be when the Exchange Online starts a communication process to the public IP of the Exchange on-Premises server. In this case, the Exchange Online server is “waiting” for a response from the IP address that was used for starting the communication channel.
An example for the static NAT rule could be:
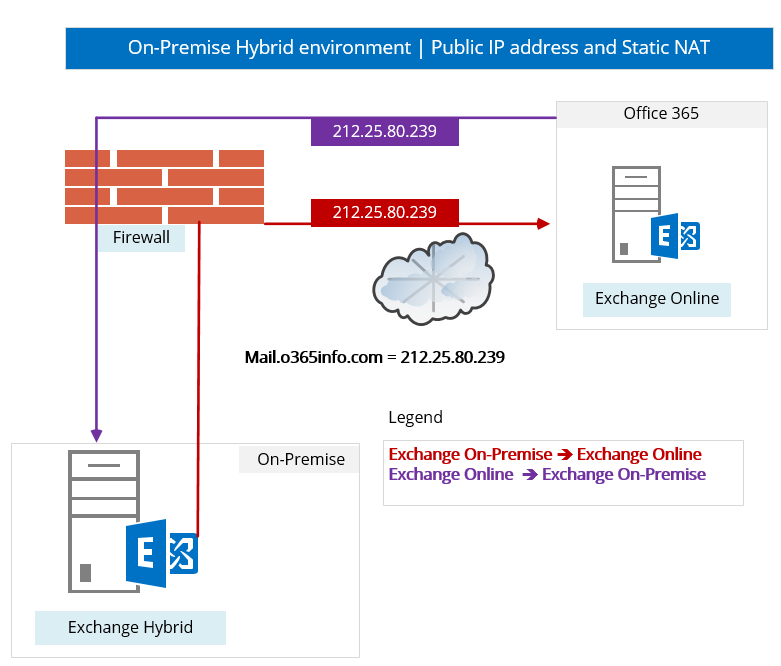
In the following diagram, we can see that when we use a static NAT rule, when external hosts such as Exchange Online try to communicate with the Public IP of the Exchange On-Premise server, the “response” from the Exchange on-Premises server, will be implemented by using the same public IP address that we use for “publishing” the Exchange on-Premises server.
Verify what is the Public IP address that the Exchange on-Premises server uses
In case that we want to be sure that the Exchange on-Premises server “respond” or access external network by using the Public IP address that was assigned for him (to verify that the Static NAT rule is configured correctly), we can use a free service that is offered by many web sites, that will enable us to get the Public IP that is used by specific internal hosts.
All we need to be open a browser search page from the Exchange On-Premise server and type: “what is my IP”
In the following screenshot, we can see “what is the Public IP” of the Exchange on-Premises server.

5. ISA-TMG server and a Firewall server
When using ISA\TMG server to publish an Exchange On-Premise server, the configurations are a little bit different compares to a “standard Firewall” because, ISA\TMG is a Proxy server and additionally, Firewall server.
When using a “Standard Firewall” we redirect the communication to the internal Exchange On-Premise server by using a simple “access rule”.
When using ISA\TMG Firewall, redirection to the internal Exchange On-Premise server is implemented by using a: Web publishing rule.
The ISA\TMG web publishing rule relates to a specific or pre-configured Exchange On-Premise “path” such as: OWA, EWS and so on.
Additional component that is used in the ISA\TMG environment is the Authentication settings. Because ISA\TMG is a proxy server, many times the configuration of the authentication process is implemented in the following way: external host authenticates (provide his credential) to the ISA\TMG, the ISA\TMG server approves or disapproves the credentials and if the complete successfully ISA\TMG will “forward in” the communication request of the external hosts.
In hybrid environment, this configuration will cause problem and errors. In simple words: when we publish Exchange On-Premise server using ISA\TMG server, we need to cancel or disable the option in which ISA\TMG server is authentication external host’s communication request.
1. ISA\TMG & Authentication settings
The communication between Exchange Online and Exchange on-Premises server (and vice versa) is implemented by creating an encrypted communication channel and, by enabling each of the sides to authenticate and identify each other.
We need to enable this “channel” to exist without any interruption or Intervention.
ISA\TMG server is a proxy server that is sometime is configured to enforce authentication process for the end point or, the host who wants to communicate with “internal host.” When relating to Hybrid environment and to a scenario in which the ISA\TMG publishes the Exchange on-Premises server, we need to cancel the setting that enforces the external endpoint to “authenticate to the ISA\TMG server.
When using the ISA\TMG rule for publishing Exchange on-Premises server AutoDiscover and EWS services, we need to verify that the TMG web publishing rule is configured with the setting: No delegation, but the client may authenticate directly.
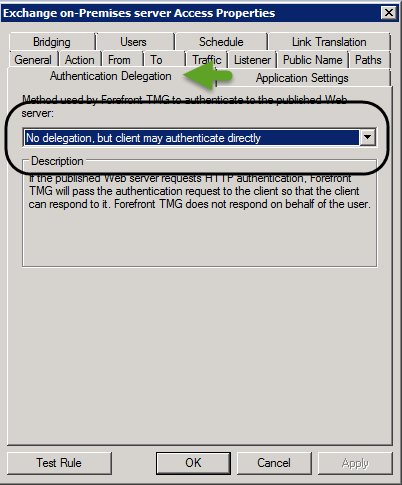
2. ISA\TMG | Exchange On-Premise | Web Publishing rule and Path
When using ISA\TMG Firewall to publish internal hosts such as Exchange On-Premise, the “access rule” is implemented by a Web Publishing rule.
The ISA\TMG Web publishing rule includes parameters such as: the name\IP of the internal host (Web Server) that we want to publish and additionally, a specific path of the web server.
In a Hybrid environment, it’s important to verify that the ISA publishing rule includes the following path:
/ews/*
/Autodiscover/*
The ISA\TMG web publishing rule should be configured to enable access to additional Exchange On-Premise web services such as OWA, Active Sync and so on.
When relating to Hybrid configuration scenario, the relevant virtual folder that needs to be configured in the ISA\TMG rules are the EWS and the AutoDiscover folders.
In the following screenshot, we can see an example for ISA\TMG web publishing rule that includes the required “Path” to the Exchange On-Premise services.

Reference from Microsoft article
The following screenshot is taken from a public Microsoft article.
In the following table we can see reference for the:
- Path name that need to be added to the ISA\TMG publishing rule
- Authentication – the need to disable or cancel the ISA\TMG feature that require
Authentication (and instead, let the client to authenticate directly before the Exchange On-Premise server)
Additional reading
- Publishing Exchange Server 2013 using TMG
- Publishing Exchange Server 2010 with Forefront UAG and TMG
- Publishing Exchange Server 2010 with Forefront Unified Access Gateway 2010 and Forefront Threat Management Gateway 2010
- Setting up Hybrid configuration without TMG
- How to Configure TMG for Office 365 (Exchange) Hybrid deployments
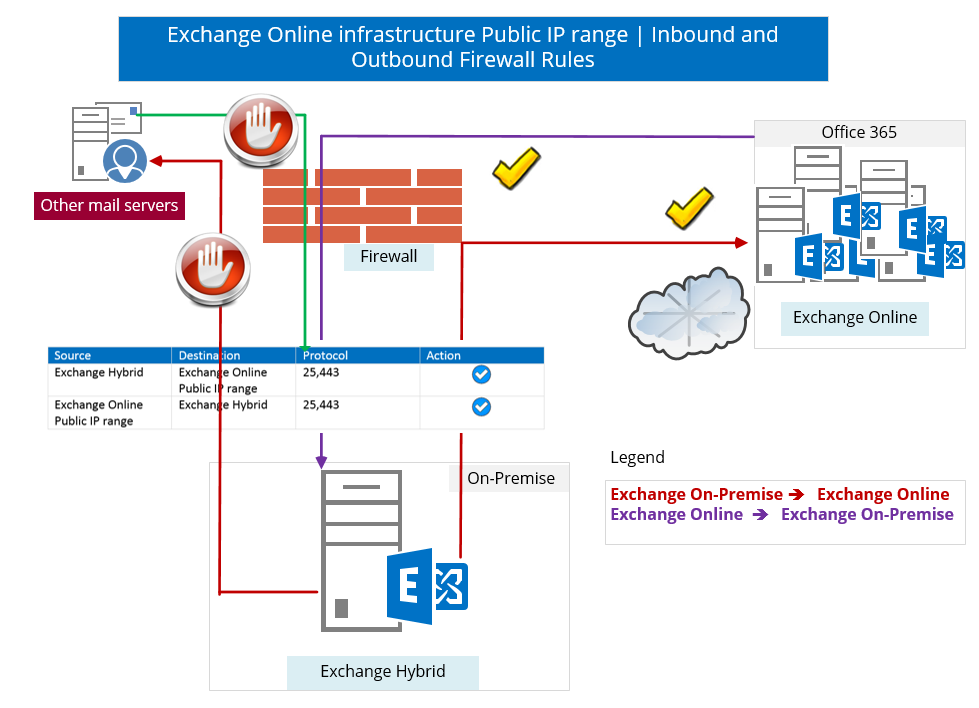
6. Firewall inbound and Outbound access policy | Office 365 and Exchange Online Public IP range
In many organizations, because of a regulation or other security requirements, there is an implementation of outbound and inbound policy that restricts access only to a dedicated or a predefined IP range.
For example: when we say:” Exchange on-Premises server is creating a communication channel with Exchange Online”, what does is mean from the “IP range” point of view?
Does Exchange Online infrastructure represented by a specific or a predefined public IP range?
The answer to this question is: “Yes.”
All the Office 365 environment such as the Windows Azure Active Directory, Exchange Online, and SharePoint Online and so on is based on a “publish” or well-known public IP range.
The implementation of Outbound and inbound firewall rules that restrict the access only to a specific or a predefined IP range consider as “good practice” from the security point of view, but can complicate and interrupt the process of the “first-time time configuration” that we use for building the “Hybrid communication channel” between the Exchange On-Premise and the Exchange Online server.
Before we start to implement a specific organizational requirement for implementing outbound\inbound policy with a restricted IP range, my recommendations are as follows:
1. TEST\Pilot Phase
In case that you are only in the Test\Pilot phase, the main purpose is to verify that we can successfully use the HCW (Hybrid configuration Wizard) for establishing the communication channel between the Exchange On-Premise and the Exchange Online (and vice versa).
In this phase, my recommendation is not to implement the outbound\inbound policy with a restricted IP range because, in case that this range is not configured properly, the Hybrid configuration wizard will fail, and it’s not so easy to find the cause of the failure.
After we successfully create all the Hybrid required settings (by using the HCW or by using PowerShell command) and verify that the communication path between the Exchange on-Premises server and the Exchange Online is “working”, you are most welcome to implement any outbound\inbound policy with a restricted IP range.
2. Learn and get familiar with the Office 365 Public IP range.
We will not get into many details about the subject of:” Office 365 Public IP range” but, it is very important to understand that the term “Office 365″, is just a logical term that defines a very complicated set of infrastructures, services, Public IP ranges and so on.
My recommendation is to read thoroughly the information about the different Office 365 infrastructures and the dedicated Public IP range that is assigned by Microsoft for each of the different Office 365 infrastructures before starting with the creation of Firewall rules, Network range and so on.
| Articles Links table | |
|---|---|
| Prepare your on-Premises environment | Public IP Address Ranges | |
| Office 365 URLs and IP address ranges | |
| Exchange Online Protection IP Addresses | |
| SharePoint Online URLs and IP Addresses | |
| Lync Online URLs and IP Address Ranges | |
| Office 365 URL based filtering is just better and easier to sustain | |
| Articles Links table | |
|---|---|
| Prepare your on-Premises environment | Port numbers | |
| Ports and protocols used by Office 365 | |
| Hybrid deployment – open ports and configuration | |
| What firewall ports do I need open to connect to Office 365 for Education? | |
| Change notification for Office 365 URLs and IP address ranges | |
3. The dynamic nature of the Public IP range
Office 365 is a dynamic environment. The basic assumption is that from time to time, there will be updated that relate to the Office 365 public IP range. To be able to stay updated and to be notified about features or current update that relate to the Office 365 Public IP ranges, you can subscribe to the following RSS feeds:
| Articles Links table | |
|---|---|
| Prepare your on-Premises environment | RSS Feed | |
| Subscribe to the Office 365 URLs and IP Address feed | |
| Office 365 Service Health RSS Notifications | |
A quick reference for the article series
| Hybrid deployment in Office 365 | Checklist and pre requirements | Part 2/3 This is the second article in the three article series deal with the pre requirement that we need to check and very before the implementation of Exchange hybrid environment. In the second article, we review additional factors and components such as:
|
|
| Hybrid deployment in Office 365 | Checklist and pre requirements | Part 3/3 This is the Third article in the three article series deal with the pre requirement that we need to check and very before the implementation of Exchange hybrid environment. The article was written as a “checklist” list” that enables us to get a summary view about the components, and the infrastructure that we need to check and verify. Additionally, the article includes a link to a word document (Hybrid deployment in Office 365 Checklist document) that you can download and use for the Hybrid configuration checklist |
We really want to know what you think about the article
The post Hybrid deployment in Office 365 | Checklist and pre requirements | Part 1/3 appeared first on o365info.com.