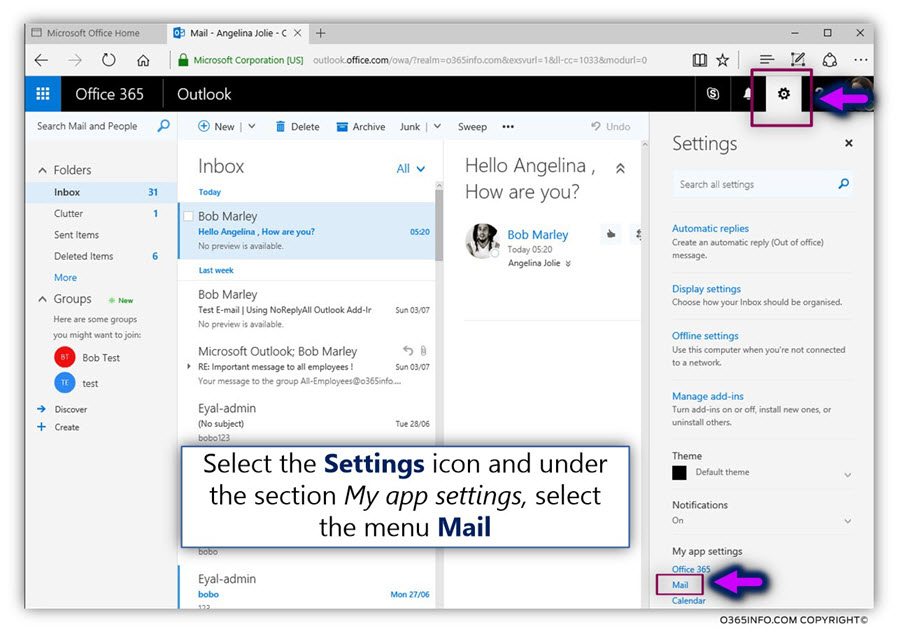
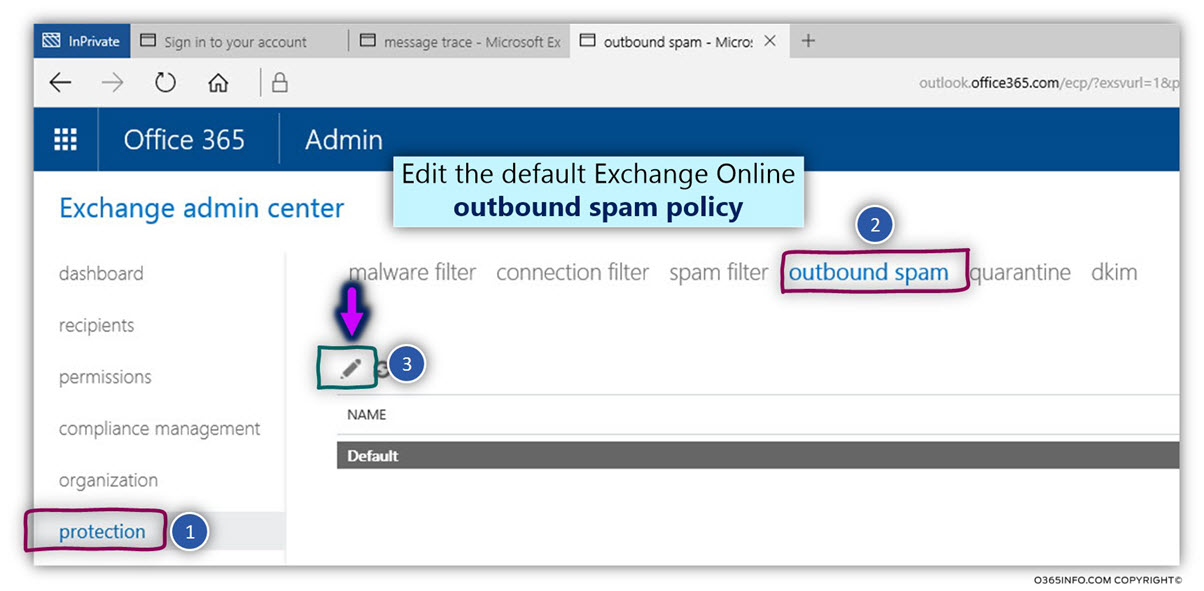
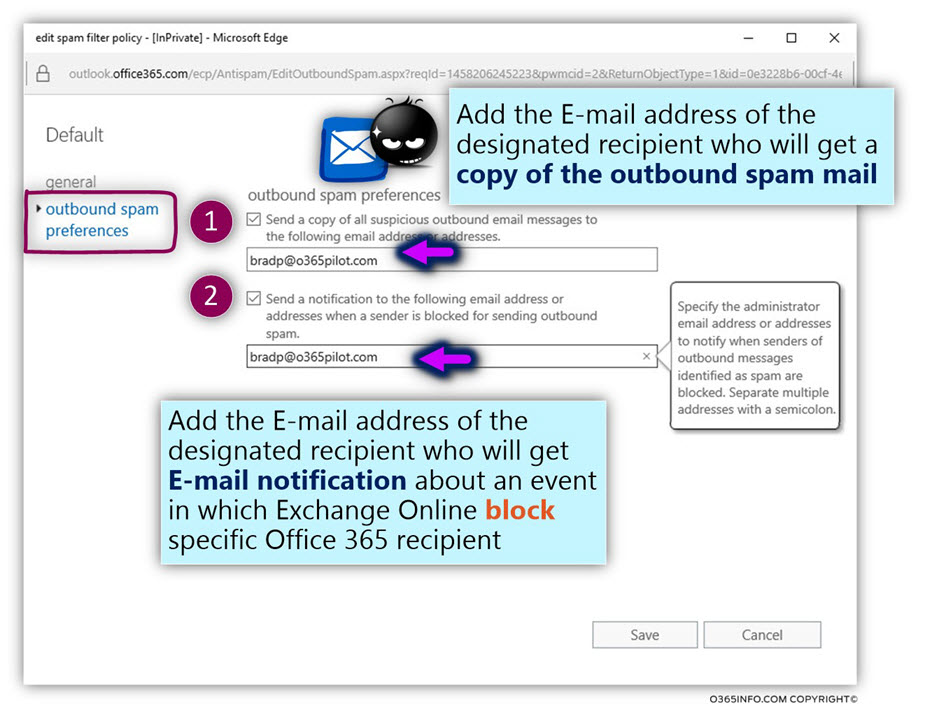
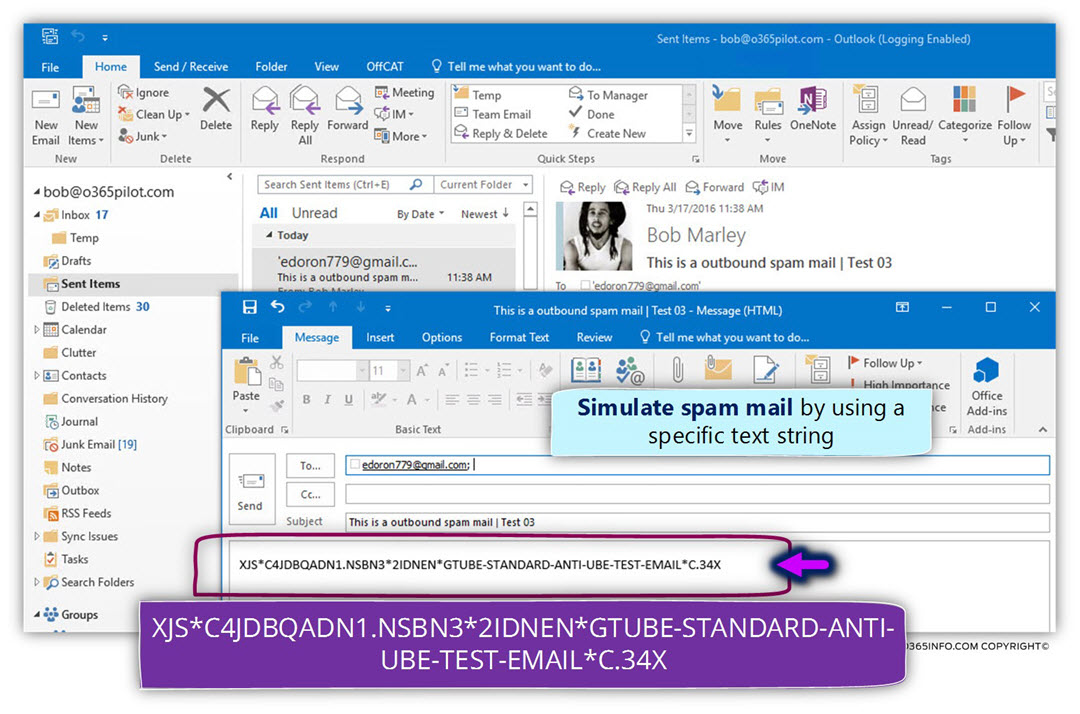
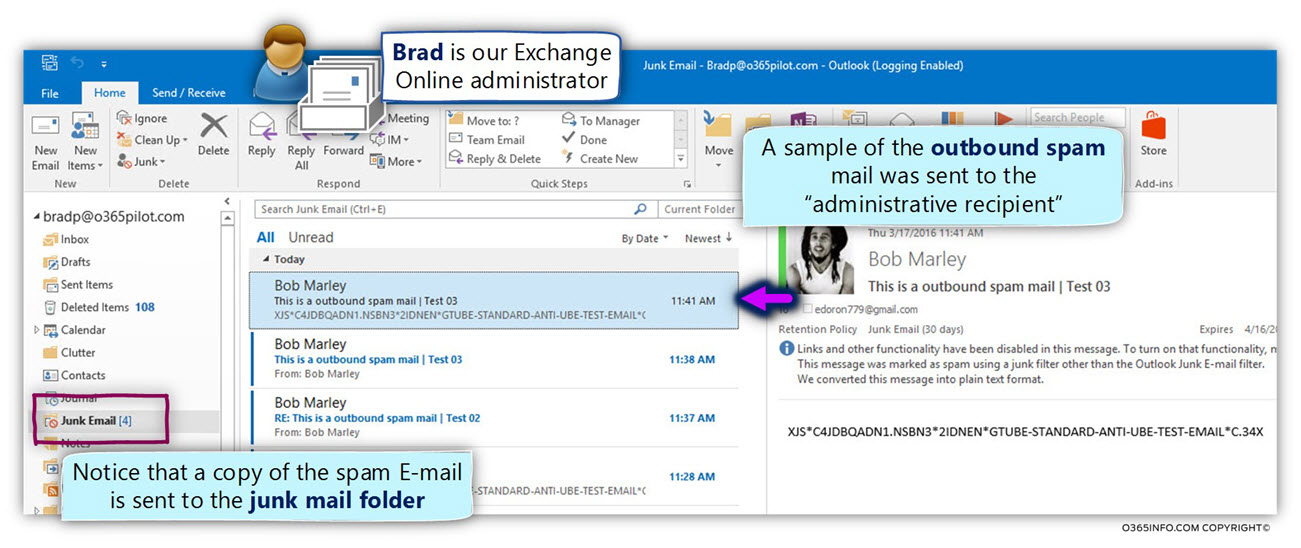
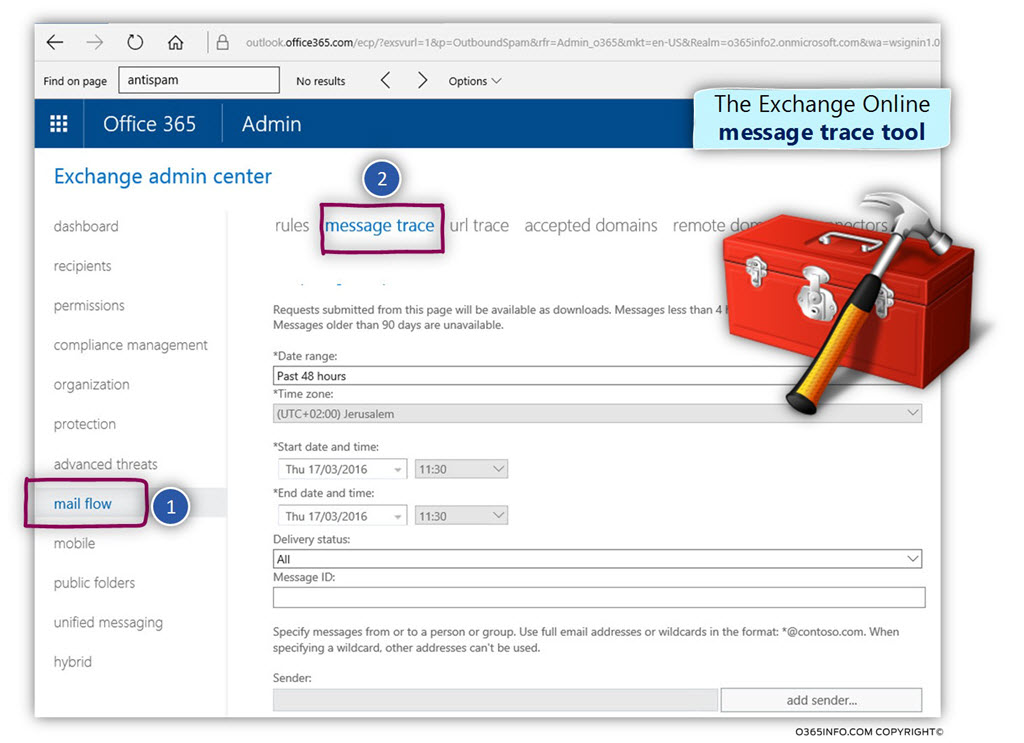
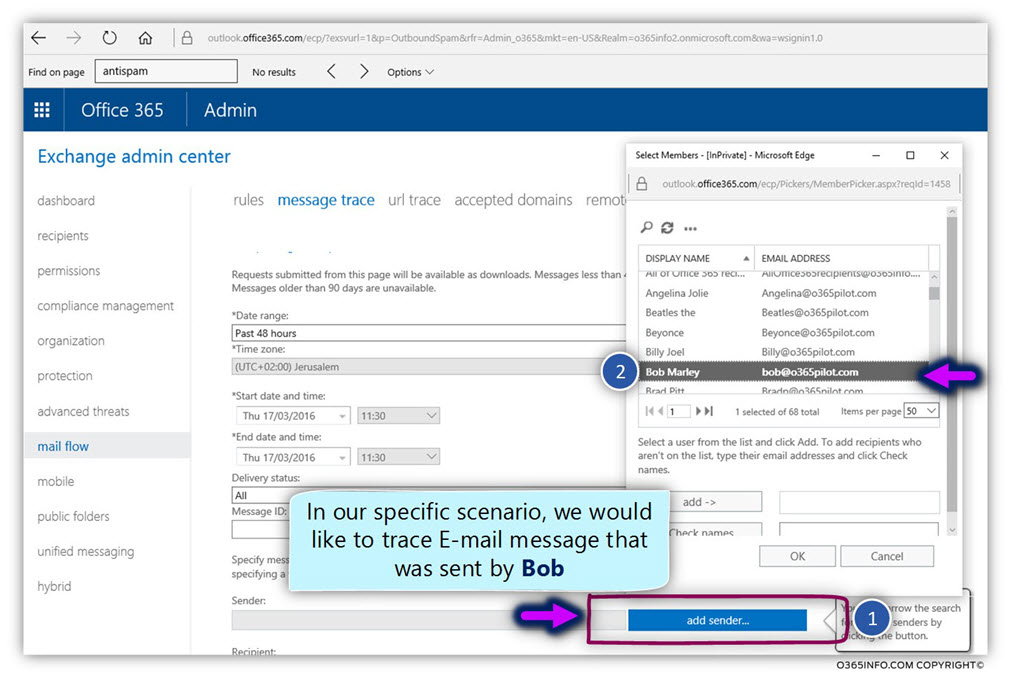
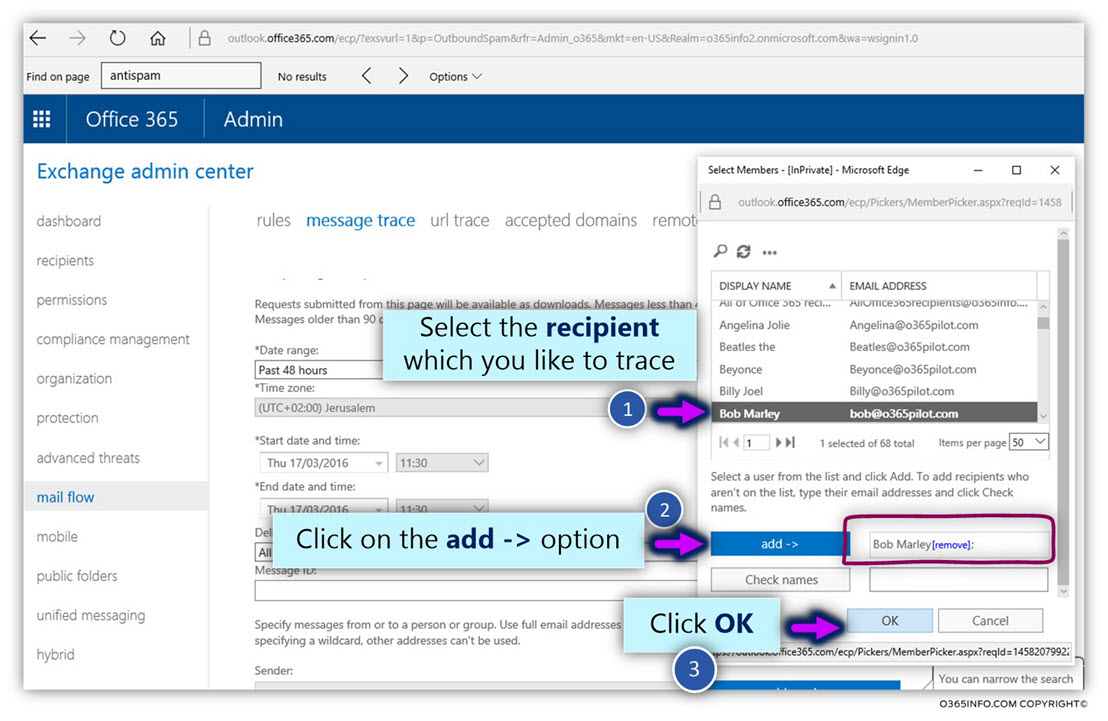
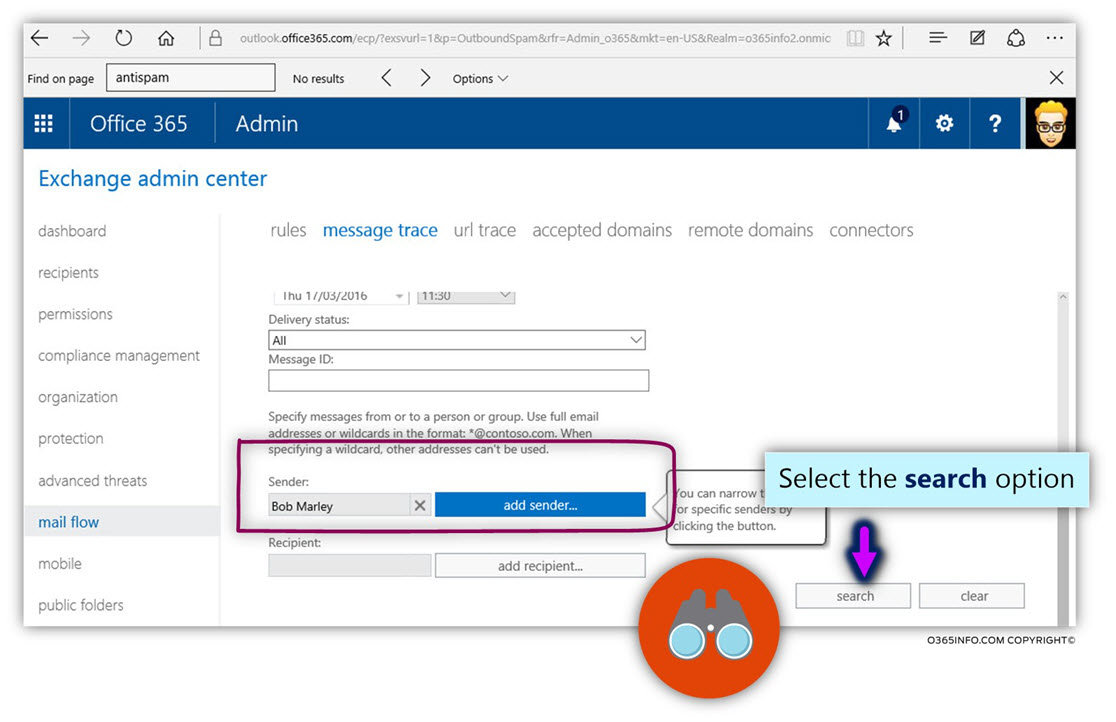
In the current article, I would like to review the possibility of a scenario which can be described as Mail loop (other common terms are – Mail storm or “reply back loop”) when using the option of Automatic Reply.
Article table of content | Click to expand
Article Series table of content | Click to expand
Manage Automatic Reply in Office 365 and Exchange Online| Article Series
The term “Mail loop” and Automatic Reply scenario
The term “Mail loop” describes an unwanted scenario, in which two recipients are configured to respond with Automatic Reply.
When recipient A Send E-mail to recipient B, recipient B responds with an “Automatic Reply.”
When the E-mail sent to recipient A, recipient A response with an ” Automatic Reply.”
Theoretically, the mail transaction between the two recipients can go on forever!
![The results of E-mail storm The results of E-mail storm]()
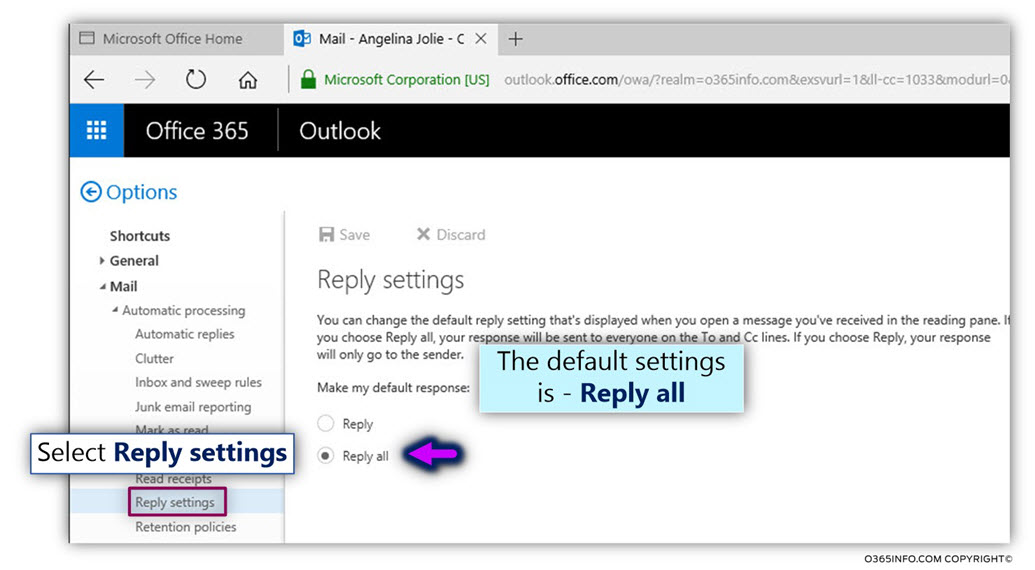
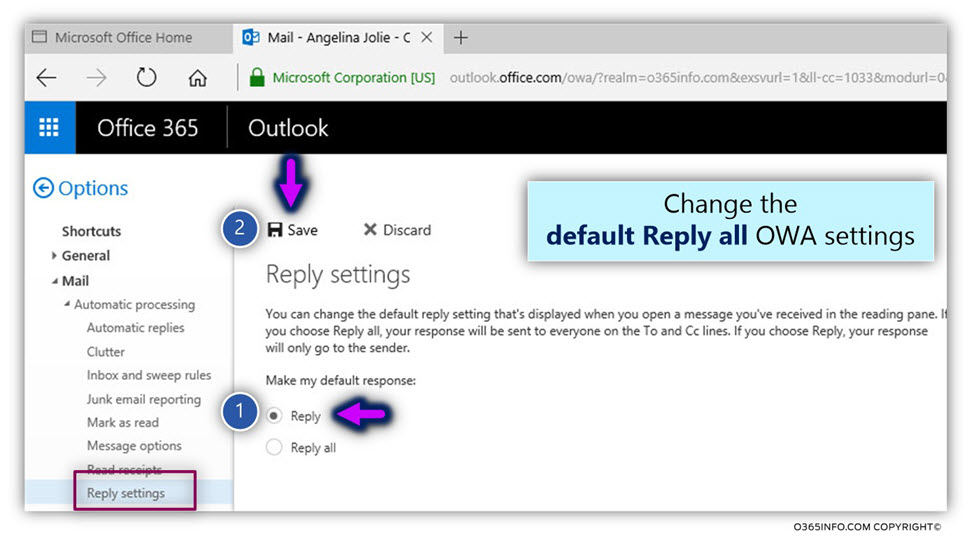
Mail loop Automatic Reply and mail standard.
To be able to deal (preventing) such “Mail loop” scenarios, the SMTP protocol RFC includes a description of the required “mail fields” that are needed to be added to an E-mail message, by the “hosting mail server” when the E-mail sent as a consequence of Automatic Reply configuration.
The information that is “inserted” by the hosting mail server, which sends the Automatic Reply
E-mail should be read by the destination mail server.
In case that the destination recipient also uses the configuration of Automatic Reply, the receiving mail server will be responsible for preventing the phenomena of “Mail loop.”
Q1: So if mail servers “know how to deal” with Automatic Reply E-mails, is it possible that a mail loop scenario will occur?
A1: Yes, in case that the “client side” meaning the mail infrastructure that sends the Automatic Reply E-mail isn’t aware of this need and doesn’t add the required information to the E-mail header, there is a possibility of the scenario of a mail loop.
Another possible scenario is related to the “destination recipient mail infrastructure.” In case that the “receiving mail server,” doesn’t know how to read or interpret information that exists in the
E-mail message header of the Automatic Reply E-mail, there is a possibility for a scenario of a mail loop.
How to prevent the scenario of “Mail loop \storm” the formal SMTP RFC recommendation
The guys who create the SMTP protocol thought in advance about such a scenario.
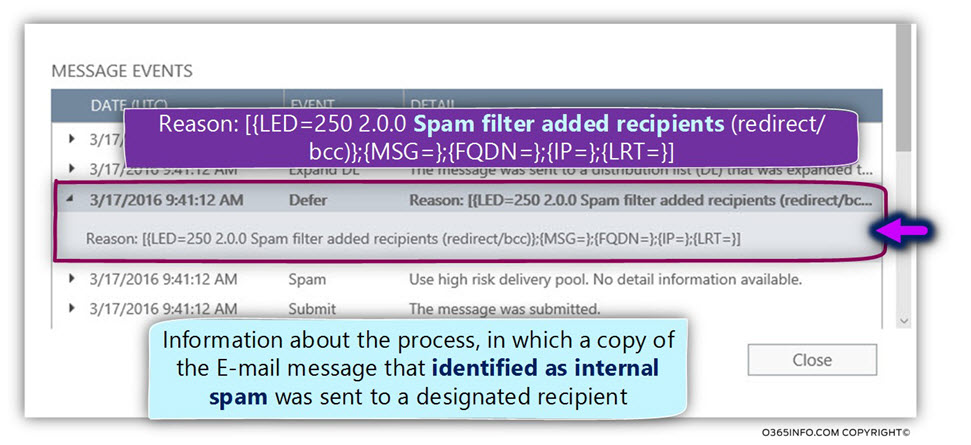
The formal SMTP RFC specification, include a dedicated mail filed named Auto-Submitted, that was created especially for “Automatic Reply” scenario.
The purpose of the Auto-Submitted mail field is, to contain a value that will help the destination mail server, to “understand”, if a specific E-mail message is a “standard E-mail” or an E-mail that was created was some Automatic response process.
In case that the E-mail sent because of “Automatic response process,” the originating mail server, that sends the E-mail, should add to the E-mail header the
Special E-mail field Auto-Submitted with a required value such as –auto-replied
The use of Auto-Submitted mail feild, is implemented as follows:
- Source mail server
When we define the configuration of “Automatic Reply” for a specific mailbox, each time that the “Automatic Reply” setting is activated, the mail source server should add the Auto-Submitted
mail field to the E-mail that is sent and define and use a predefined value
such as – auto-replied or auto-generated.
- Destination mail server \ destination recipient
When the E-mail message reaches to the destination mail server, and the destination mail server “notice” that the E-mail is supposed to be sent to a recipient who also uses “Automatic Reply” configuration, the destination mail server, should decide if he wants to stop\prevent the “Automatic Reply” E-mail or send the automatic response only one time.
In other words, because that the sender E-mail header includes the mail field – Auto-Submitted and the value of auto-replied (or auto-generated, and because the destination recipient uses an “Automatic Reply” configuration, the receiving mail server should prevent the automatic respondent from being sent to the “original sender.”
Attached some quotes from the SMTP RFC:
Automatic responses SHOULD NOT be issued in response to any message which contains an Auto-Submitted header field (see below), where that field has any value other than “no”.
The Auto-Submitted field, with a value of “auto-replied“, SHOULD be included in the message header of any automatic response.
The purpose of the Auto-Submitted header field is to indicate that the message was originated by an automatic process, or an automatic responder, rather than by a human; and to facilitate automatic filtering of messages from signal paths for which automatically generated messages and automatic responses are not desirable.
The auto-generated keyword:
– SHOULD be used on messages generated by automatic (often periodic)
processes (such as UNIX “cron jobs”) which are not direct
responses to other messages,
– MUST NOT be used on manually generated messages,
– MUST NOT be used on a message issued in direct response to another
message,
– MUST NOT be used to label Delivery Status Notifications (DSNs)
[I2.RFC3464], or Message Disposition Notifications (MDNs)
[I3.RFC3798], or other reports of message (non)receipt or
(non)delivery. Note: Some widely-deployed SMTP implementations
currently use “auto-generated” to label non-delivery reports.
These should be changed to use “auto-replied” instead.
[Source of information –
Recommendations for Automatic Responses to Electronic Mail]
Dealing with a scenario of “Mail loop \ Storm” – Exchange based environment | Server side.
Just a quick reminder, in Exchange base environment, there are two major ways for implementing a solution of – Automatic Reply.
- Automatic replies (Out of office assistant)
- Automatically respond using inbox rule
Exchange server, relate to the subject of “Mail loop\Storm” when using automatic response using two aspects:
Exchange infrastructure | Outgoing mail | Automatic response behavior
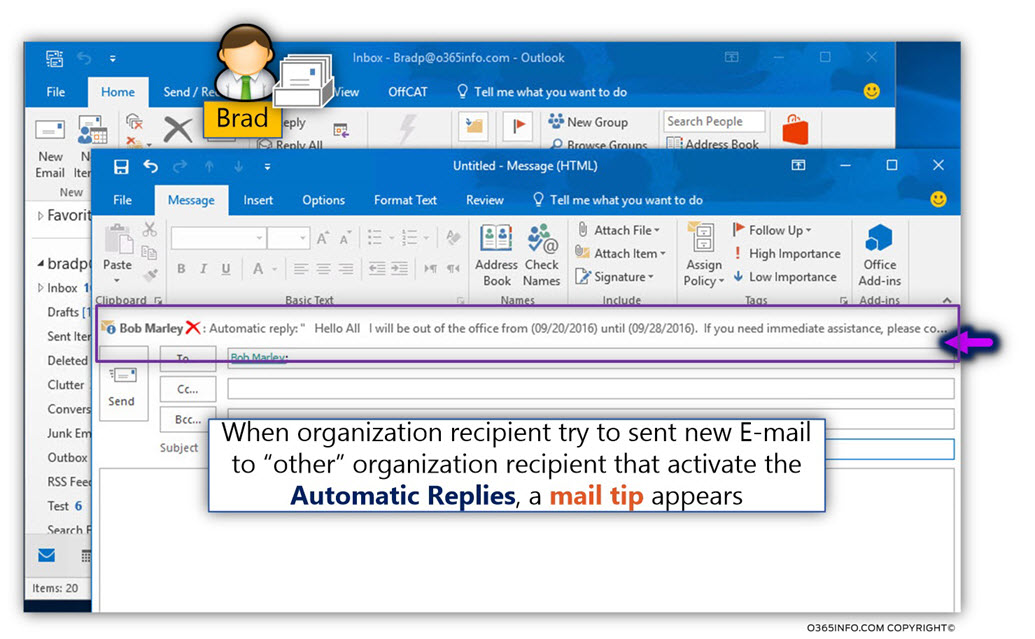
In case that the Exchange recipient uses the option of – Automatic replies (Out of office assistant), each time that the “Out of office” E-mail message is sent to the specific sender, the information is “registered” in Exchange server.
In case that the same sender sends an additional E-mail, the Automatic replies (Out of office assistant) response will not send again.
This process was created for – preventing the scenario in which the same E-mail will be sent over and over to the same sender, and in addition, prevent a scenario in which the “original sender” use the option of automatic response E-mail.
The Out of Office Assistant sends an automatic reply to notify users who send you messages that you are away from the office.
Your reply is only sent once to a message sender.
The count is reset when you toggle the Out of Office Assistant.
Microsoft Exchange clears its internal “sent to” list when you disable the Out of Office Assistant.
If you would like to have a reply sent for every message, use Rules instead of the Out of Office Assistant.
[Source of information –
Only one reply is sent to each sender when the Out of Office Assistant is enabled]
An additional mechanism that is implemented by the Exchange for outgoing E-mail that was generated by Automatic replies (Out of office assistant), is adding a specific mail field and values to the E-mail message. We will review this method in the next section.
Automatically respond using inbox rule
In a scenario in which Exchange user implements the option of – Automatic reply using mailbox rule, Exchange server doesn’t keep any information about an event in which E-mail was already sent to s specific recipient.
In other words, in case that Exchange user configures the Automatic Reply mailbox rules, and in case that a specific sender sends E-mail couple of times, the mailbox rule will be activated each time.
Q1: Can we assume that in a scenario in which the sender also uses an Automatic Reply, that the result will be “Mail loop \ Storm”?
A1: Most of the time, the answer is “No.” In another word, most of the time, Exchange servers will know how to prevent a scenario of “Mail loop \ Storm.”
The basic assumption is that the “source mail server” (the originator mail server) will add the required E-mail field to the E-mail header. The “Automatic Reply mail fields,” will enable the destination Exchange server who gets the E-mail on behalf of the recipient, to “understand” that the E-mail was sent as “Automatic Reply.”
In case that the destination recipient (the Exchange recipient) also uses Automatic reply, the mailbox rule will be activated only once.
Exchange infrastructure | Outgoing mail | Automatic response behavior
The other side of the equation is the procedure that Exchange server uses for “outgoing mail” that was created as a result of the Automatic responder using inbox rule or when using the option of – Automatic replies (Out of office assistant).
In this scenario, Exchange server adds to the E-mail header, a specific mail field with a specific value that should be used by the “destination mail server.”
Exchange server uses a combination of “standard SMTP RFC” recommendation + a dedicated Exchange mail field.
The purpose of these mail fields is – to “signal” the receiving mail server that a specific E-mail
Is an E-mail that was generated as an automatic response.
- In case that the destination mail server is an Exchange based server, he will “know” how to relate to the “Exchange dedicated mail field.”
- In case that the destination mail server is not an Exchange based server, he will relate to the “SMTP standard” mail field the Auto-Submitted mail field with the
value –auto-generated
Automatic response mail field’s Exchange versus Gmail
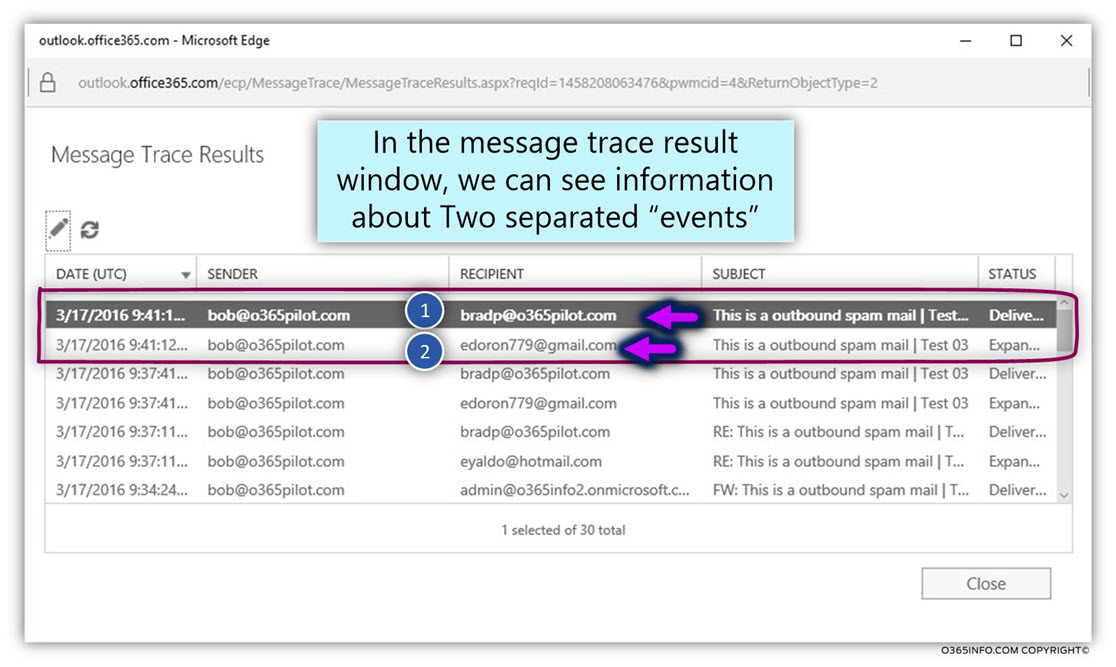
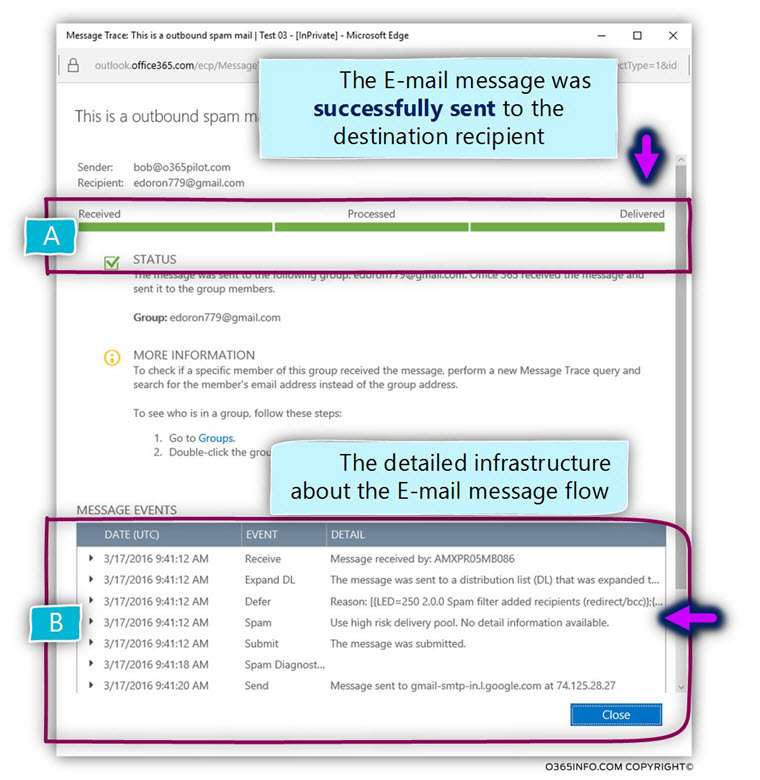
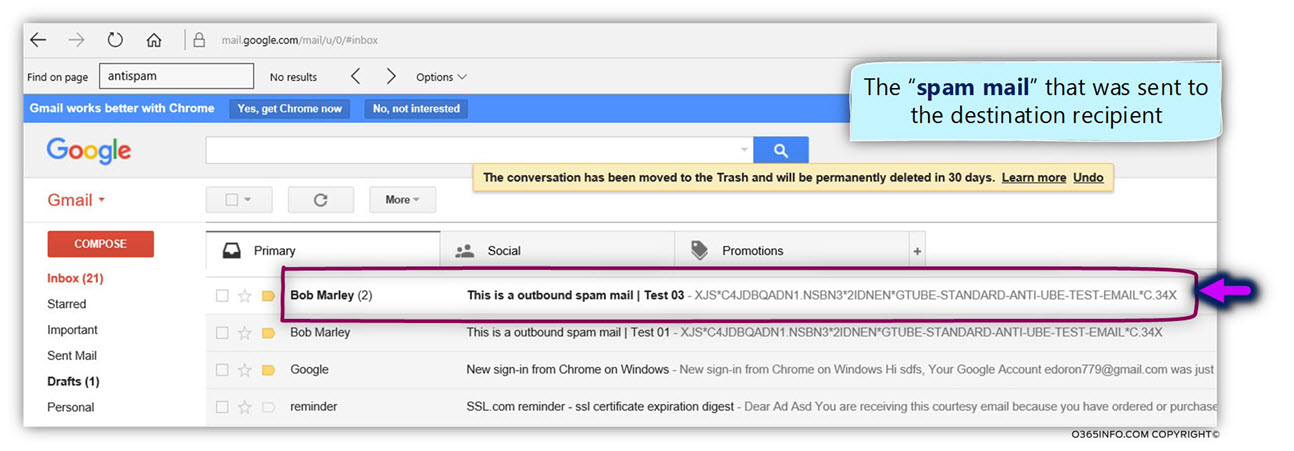
Testing Automatic Reply E-mail process in a Exchange Online based environment
To be able to understand better the way that Exchange server use for “stamping” E-mail message that was created as a result of Automatic reply, I have configured two Exchange Automatic reply options:
- Exchange mailbox to use – Automatic replies (Out of office assistant)
- Exchange mailbox to use – Automatic respond using inbox rule
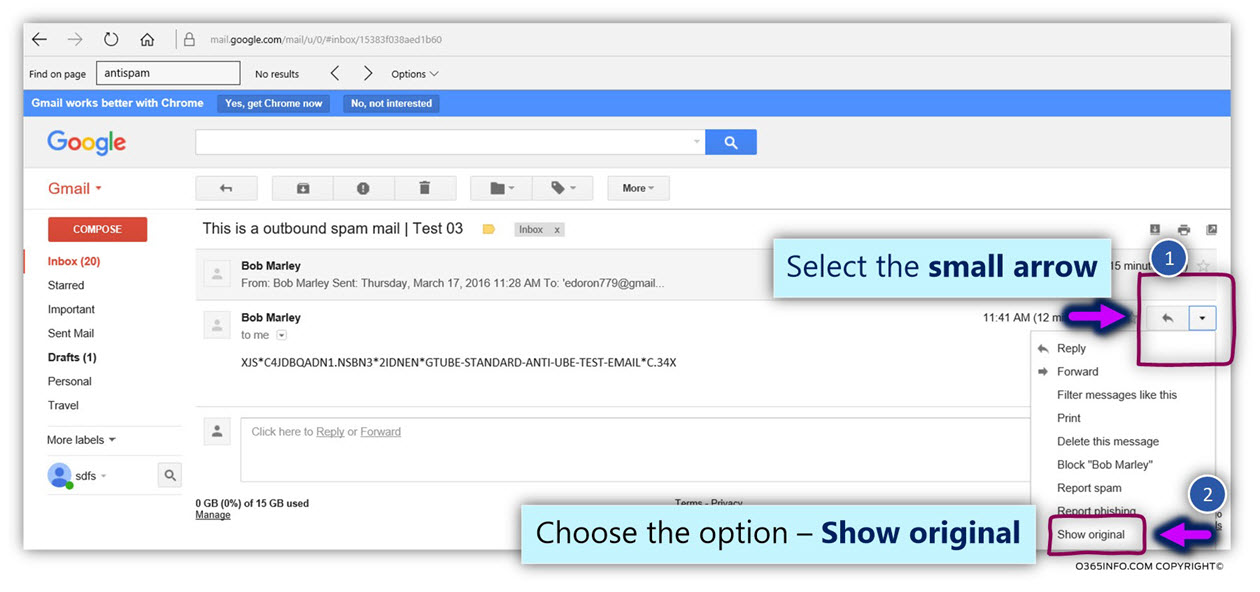
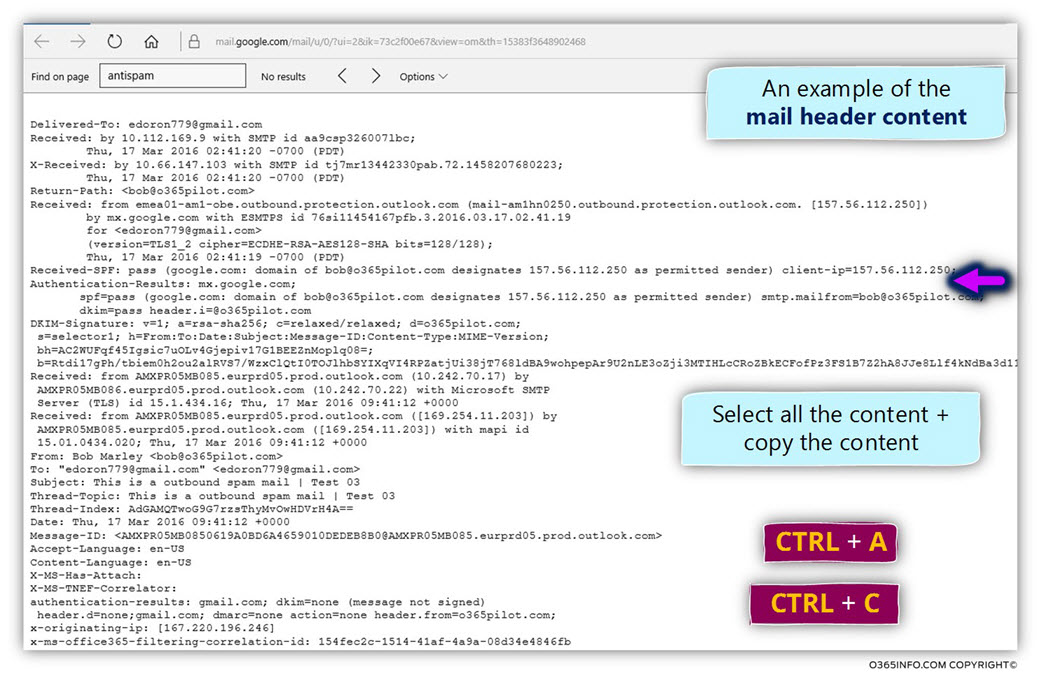
I have generated the process of “Automatic Reply E-mail” that was sent to the destination recipient, get the E-mail address header that was sent to the destination recipient, and analyze the information that was added to the E-mail header (the E-mail that was generated as Automatic Reply E-mail)
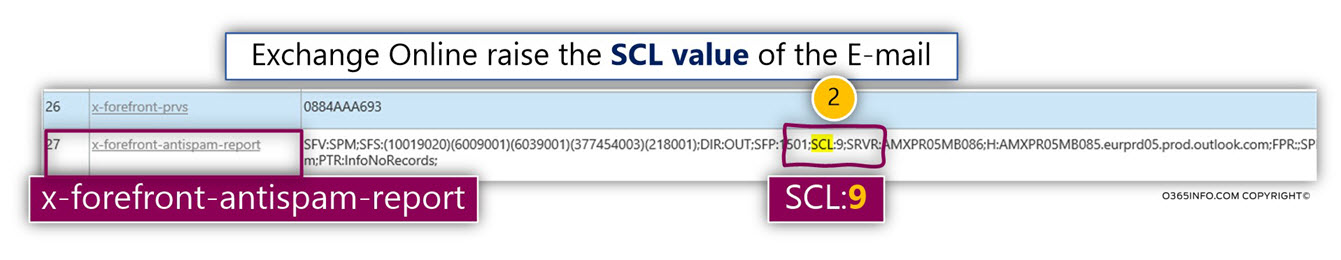
The mail fields that Exchange server generates that relate to processing of Automatic Reply are as follows:
| Mail Fields |
Value |
Exchange or SMTP RFC |
| X-Auto-Response-Suppress |
all |
Exchange |
| X-MS-Exchange-Inbox-Rules-Loop |
<Recipient E-mail address> |
Exchange |
| auto-submitted |
auto-generated |
SMTP RFC |
| x-ms-exchange-generated-message-source |
Mailbox Rules Agent |
Exchange |
A couple of “insight” from the information that was “reviled” in the E-mail header:
- The E-mail fields that relate to Automatic Reply are identical when using the option of Automatic replies (Out of office assistant) versus the option of Automatic responder using mailbox rule. My assumption was that Exchange server would use different mail fields or different values for each of the separated Automatic Reply options, but when looking at the data, there is no difference between the E-mail fields that relate Automatic Reply.
- There is very little information on the public network about the characters or the purpose of the “Exchange mail fields” that are used in E-mail that was generated as Automatic Reply. When I try to look for detailed information about this “Exchange mail fields,” I could not find helpful information that will explain clearly the role of each mail field.
- Exchange server uses the standard SMTP RFC mail field that “stamp” E-mail as an Automatic Reply by using the mail field “auto-submitted” and the
value “auto-generated”.
Testing Automatic Reply E-mail process in a Gmail based environment
To be able to understand better how another mail infrastructure such as Gmail relates to the subject of Automatic Reply and mail fields, I use a Gmail account and activate the option named – “Out of office or vacation reply.”
When we look at the mail header of the E-mail that was sent from a Gmail account as a result of an Automatic Reply E-mail, we can find the following mail fields that relate to the “Automatic Reply” process:
| Mail Fields |
Value |
Exchange or SMTP RFC |
| X-Autoreply |
Yes |
Gmail \other |
| auto-submitted |
auto-replied |
SMTP RFC |
A couple of “insights” from the information that was “reviled” in the E-mail header:
- Gmail mail server uses a “non SMTP RFC” mail filed named – “X-Autoreply” with the value “Yes.”
- Gmail mail server uses the standard SMTP RFC mail field that “stamp” a specific E-mail as an Automatic Reply, by using the mail field “auto-submitted” and the
value “auto-replied”.
Additional reading
Gmail – Automatic Reply
auto-submitted
X-Auto-Response-Suppress
X-MS-Exchange-Inbox-Rules-Loop
Mail loop \storm | Real life scenario | Testing Automatic response behavior in different scenarios
One of the main “issues” in a scenario in which we use Automatic Reply using mailbox rule, relate to the concern about a possible scenario of “Mail loop” or “Mail storm.”
In case that booth of the sided (the sender and the recipient) is configured to use Automatic Reply, this configuration could lead to a scenario of “Mail loop.”
Assuming the both of the side supports the SMTP RFC and the RFC “instructions” that relate to Automatic Reply mail fields, and the source mail server “stamp” the E-mail Hader with information about the fact the E-mail considers as an Automatic response, the scenario of “Mail loop” or Mail storm” should not be realized.
Because most of the time, we cannot be sure about the “other side” (the other involved mail infrastructure) marks correctly Automatic Reply E-mail, I have tried to test a couple of passable scenarios in which booths of the mail recipient using Automatic respond to settings.
To be able to verify the behavior of automatic response in an Office 365 based environment that interact with the other mail environment, I have configured Office 365 to use Automatic Reply by using mailbox rule, and try to interact with a recipient from another mail infrastructure, that also uses Automatic Reply configuration.
- The Office 365 recipient described as – recipient A
- The other mail infrastructure recipient described as – recipient B
Booth of the recipients was configured to use Automatic Reply.
Our purpose is to verify if a scenario of “Mail loop” or “Mail storm” could be realized when Office 365 recipients interact with other mail infrastructures.
The test will be implemented in the following way:
- Recipient A (Office 365 recipient) is configured to use Automatic Reply using mailbox rule.
- Recipient A sends E-mail to recipient B.
- The E-mail should be accepted by recipient B.
- Recipient B will “respond” with Automatic Reply E-mail.
- The E-mail should be accepted by recipient A.
The “thing” that we want to check \ test is – if this scenario leads to a “Mail loop” or “Mail storm.”
Our main concern is to verify if the Office 365 user (recipient A) will continue to respond using Automatic Reply E-mail.
Scenario 1: Exchange Online environment versus Exchange Online
In this scenario, recipient A is an Office 365 recipients who belong to organization X and recipient B are also an Office 365 recipient who belong to organization Y.
In other words, although a both of the recipients is hosted at Office 365 mail infrastructure, each of the recipients belongs to a different organization.
The result
When we implement the scenario in which recipient A send E-mail to recipient B and both recipients are configured to use Automatic Reply, the scenario of “Mail loop” or “Mail storm” was not realized.
![Scenario 1 - Testing Mail loop storm -Exchange Online environment versus Exchange Online Scenario 1 - Testing Mail loop storm -Exchange Online environment versus Exchange Online]()
Scenario 2: Exchange Online environment versus Exchange on-Premises
In this scenario, recipient A is an Office 365 recipients who belong to organization X and recipient B are Exchange on-Premises recipient, that belongs to organization Y.
The result
When we implement the scenario in which recipient A send E-mail to recipient B and both of the recipient are configured to use Automatic Reply, the scenario of “Mail loop” or “Mail storm” was not realized.
![Scenario 2 - Testing Mail loop Exchange Online environment versus Exchange on-Premises Scenario 2 - Testing Mail loop Exchange Online environment versus Exchange on-Premises]()
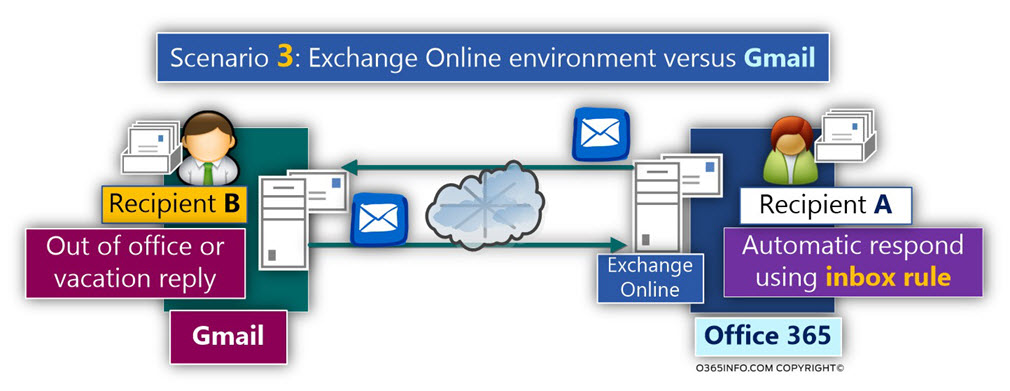
Scenario 3: Exchange Online environment versus Gmail
In this scenario, recipient A is an Office 365 recipient who belongs to organization X and recipient B, is Gmail recipient, that belongs to organization Y.
The result
When we implement the scenario in which recipient A send E-mail to recipient B and both recipients are configured to use Automatic Reply, the scenario of “Mail loop” or “Mail storm” was not realized.
![Scenario 3 - Testing Mail loop storm scenarios -Exchange Online environment versus Gmail Scenario 3 - Testing Mail loop storm scenarios -Exchange Online environment versus Gmail]()
How to detect and prevent a scenario of “Mail loop \ mail storm” that was caused by Automatic reply configuration.
Generally speaking, regarding the best practice of implementing Automatic reply configuration, the ideal scenario is a scenario, in which the mail infrastructure that sends E-mail as an Automatic reply, will “stamp” the E-mail with some information (a unique mail fields), that will inform the “other side” that the E-mail is an “Automatic reply E-mail.”
At the same time, we were expecting from the destination recipient mail infrastructure, to know how to read the “unique mail fields” that say that the E-mail is an “Automatic reply E-mail” and responds appropriately.
In case that the “source mail infrastructure” didn’t add the required information about “Automatic reply E-mail” or in case that the destination mail infrastructure doesn’t know how to relate to the specific mail fields in the header that include information about “Automatic reply
E-mail”, we could face a possible scenario of “Mail loop \ mail storm.”
To be able to prevent a “Mail loop \ Mail storm” scenario, in Exchange based environment, we can add to the Exchange Automatic reply inbox rule that we were created or to the Automatic replies (Out of office assistant), an additional “configuration layer.”
The purpose of the “additional configuration layer” is to enable the Exchange recipient to identify a scenario, in which the E-mail that reaches the mailbox is an “Automatic reply E-mail.”
![Configuring the Exchange Online mailbox to - identify Automatic Reply E-mail Configuring the Exchange Online mailbox to - identify Automatic Reply E-mail]()
In this case, we would like to “instruct” the Exchange mailbox that uses an Automatic reply mailbox rule, not to respond with Automatic Reply E-mail.
In other words, in case that the E-mail that is sent from the sender considers as Automatic Reply E-mail, don’t activate the Automatic Reply E-mail response.
Q1 – How can we identify a scenario in which the E-mail that was sent is an Automatic
Reply E-mail?
A1 -In case that the source mail infrastructure didn’t use standard mail fields for classifying the specific E-mail as “Automatic reply E-mail,” there is no mechanism that can detect such as an event in 100 percent certainty.
The good news is that there are some “tricks” that we can use, for identifying E-mail that can be considered as an “Automatic reply E-mail” because many times, this type of E-mails has a unique character.
In the following section, I would like to review some possible configuration that we can add to Exchange mailbox rule, that will try to identify as “Automatic reply E-mail.”
The configuration that we add to the Exchange mailbox rule, will be added to a section described as “exception”, which instruct the Exchange mailbox rule when not to activate the mailbox rule.
In our scenario, we will add the exceptions to the Exchange Automatic reply inbox rule that we have reviewed in the article – Setting up an Automatic Reply in Office 365 using mailbox rule and Shared mailbox | Part 5#7
Our “exceptions” will relate to three different types of scenarios:
Scenario 1 – we will add an exception that relates to a specific sender. For example, we experience a scenario of “Mail loop \ mail storm” because, external support ticket system, that uses the E-mail address – Support@thankyouforsharing.org, send E-mail automatically to one of our organization users and this “support tickets system” doesn’t comply with the SMTP RFC (the E-mail doesn’t include any indication of the fact that the E-mail is an Automatic Replay
E-mail).
Scenario 2 – our mail server doesn’t know how to identify “Automatic reply E-mail,” although the sender adds the required mail fields.
To be able to handle this scenario, we will instruct the Exchange mailbox rule, to look at the E-mail header, and look for a specific mail field that used in the case that the E-mail considers as “Automatic reply E-mail.”
Scenario 3 – We experience a scenario of “Mail loop \ Mail storm” because – external recipient sends “Automatic reply E-mail” but doesn’t add the required mail fields to the E-mail (doesn’t comply with the SMTP RFC).
This time, we will try to locate a specific keyword in the E-mail subject or the E-mail body that suggests that the specific E-mail is an “Automatic reply E-mail.”
Configuring Exchange mailbox rule exception – preventing “Mail loop \ mail storm” that was caused by Automatic reply configuration.
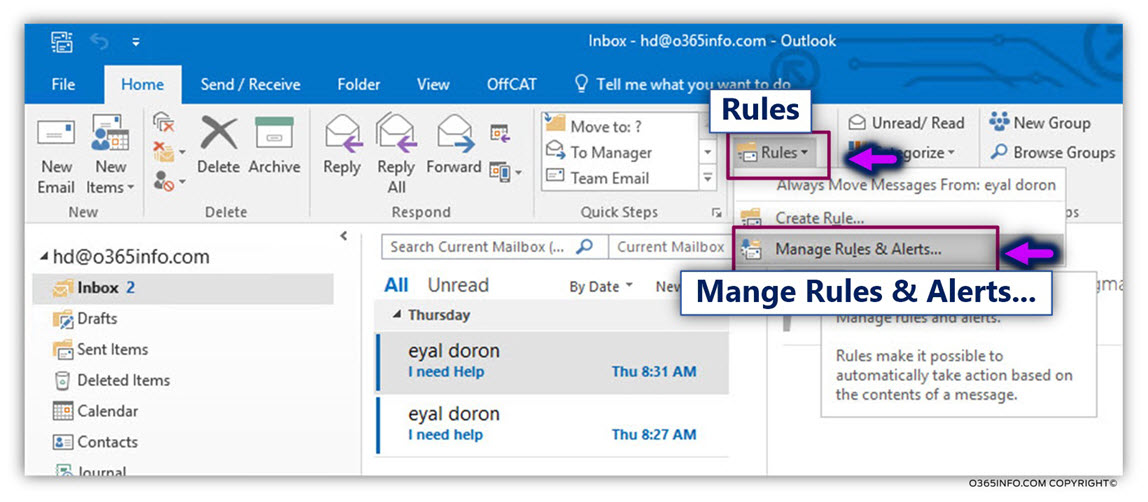
Log in to the Exchange mailbox that was configured to use the Automatic reply inbox rule.
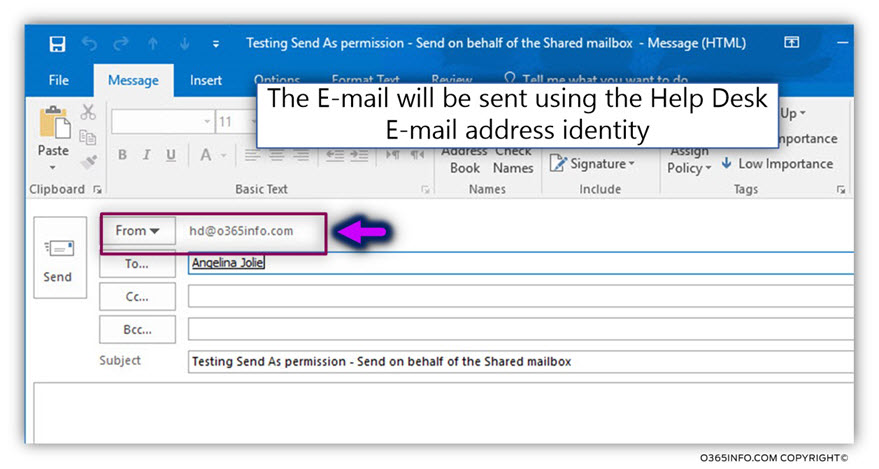
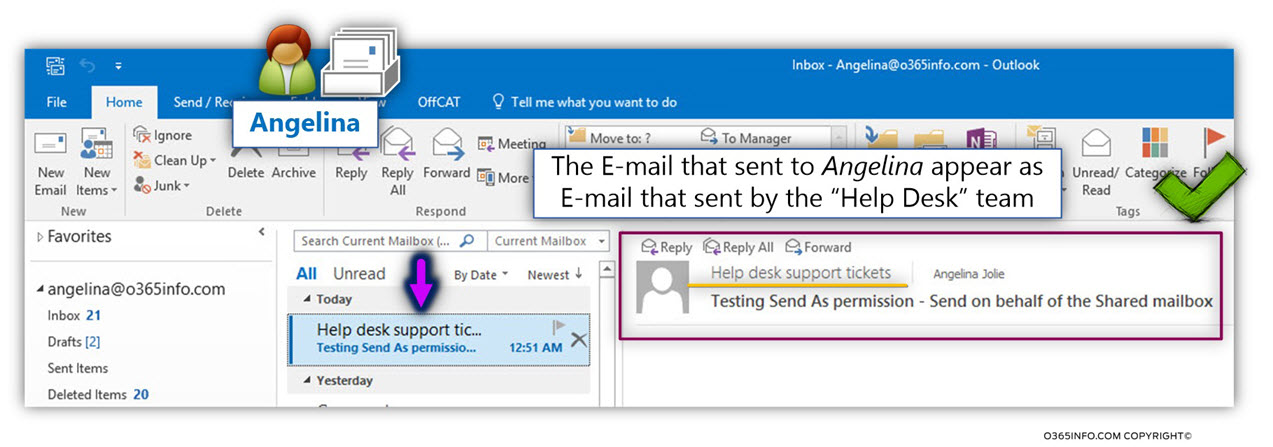
In our example, we log in to the “Help desk support tickets” shared mailbox (the Automatic reply inbox rule was created in the article – Setting up an Automatic Reply in Office 365 using mailbox rule and Shared mailbox | Part 5#7).
- Select the Rules menu
- Select the Mange Rules & Alerts… menu
![Detect and prevent a scenario of Mail loop -caused by Automatic reply – Exchange inbox rule -01 Detect and prevent a scenario of Mail loop -caused by Automatic reply – Exchange inbox rule -01]()
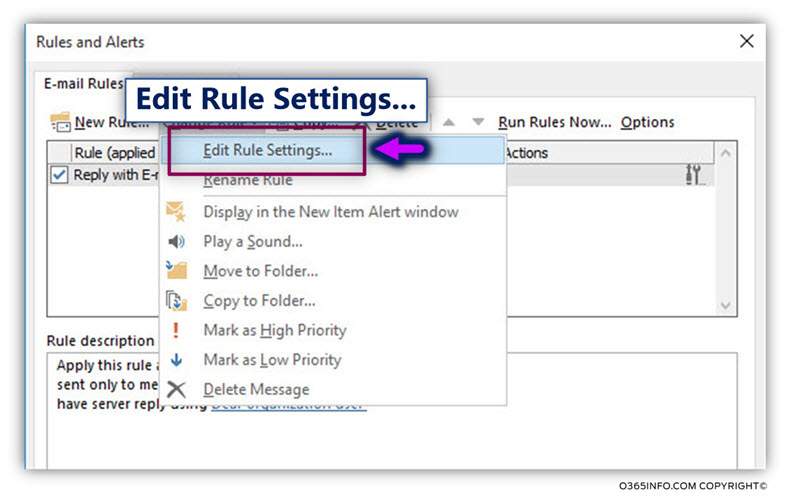
- Select – Edit Rule Settings…
![Detect and prevent a scenario of Mail loop -caused by Automatic reply – Exchange inbox rule -02 Detect and prevent a scenario of Mail loop -caused by Automatic reply – Exchange inbox rule -02]()
In our example, we edit an existing inbox rule. To be able to get to the “exception” configuration screen, we will need to go over the inbox rule condition and action.
![Detect and prevent a scenario of Mail loop -caused by Automatic reply – Exchange inbox rule -03 Detect and prevent a scenario of Mail loop -caused by Automatic reply – Exchange inbox rule -03]()
![Detect and prevent a scenario of Mail loop -caused by Automatic reply – Exchange inbox rule -04 Detect and prevent a scenario of Mail loop -caused by Automatic reply – Exchange inbox rule -04]()
Step 1#3 – Adding an exception for scenario 1 | Don’t reply if the sender is X
In this section, we define an exception that relates to a specific sender.
In our example, an external recipient is a support system, that uses the E-mail address – Support@thankyouforsharing.org.
This support system sends “Automatic reply E-mail” to one of our organizations that also uses an “Automatic reply E-mail” configuration.
Because that the sender doesn’t mention the fact that the E-mail considers as “Automatic
reply E-mail” (doesn’t add information to the E-mail header) the result
was “Mail loop \ mail storm.”
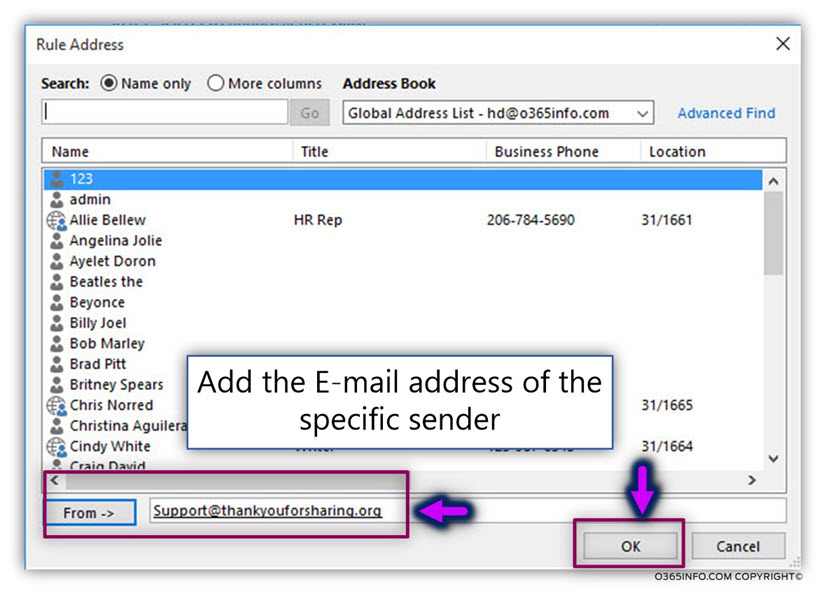
To prevent this scenario, we will add to the existing Automatic reply mailbox rule, an exception that includes the E-mail address of the source sender.
- Select the check box – except if from people or public group
![Detect -and prevent a scenario of Mail loop -caused by Automatic reply – Exchange inbox rule -05 Detect -and prevent a scenario of Mail loop -caused by Automatic reply – Exchange inbox rule -05]()
Write down the E-mail address of the recipient who will be added to the exception. Note that the E-mail address will probably will not appear in the recipient list because this is an “external recipient” E-mail address.
![Detect and prevent a scenario of Mail loop -caused by Automatic reply – Exchange inbox rule -06 Detect and prevent a scenario of Mail loop -caused by Automatic reply – Exchange inbox rule -06]()
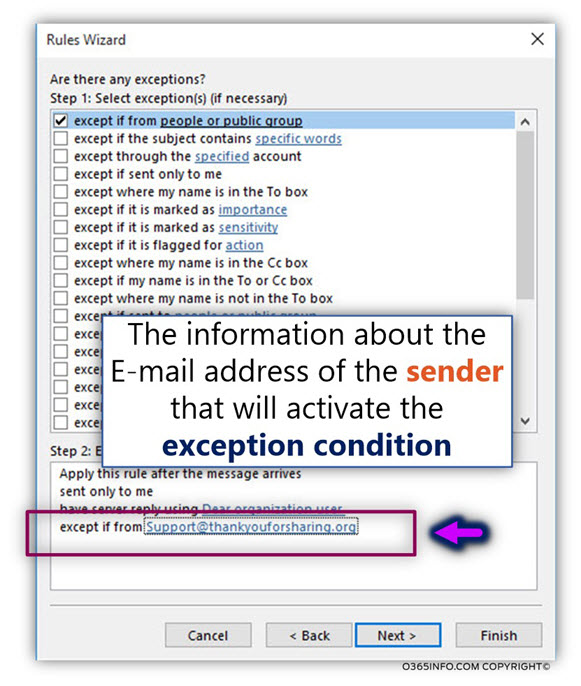
In the following screenshot, we can see that the information about the source, sender E-mail address was updated in the mailbox rule exception section.
![Detect and prevent a scenario of Mail loop -caused by Automatic reply – Exchange inbox rule -07 Detect and prevent a scenario of Mail loop -caused by Automatic reply – Exchange inbox rule -07]()
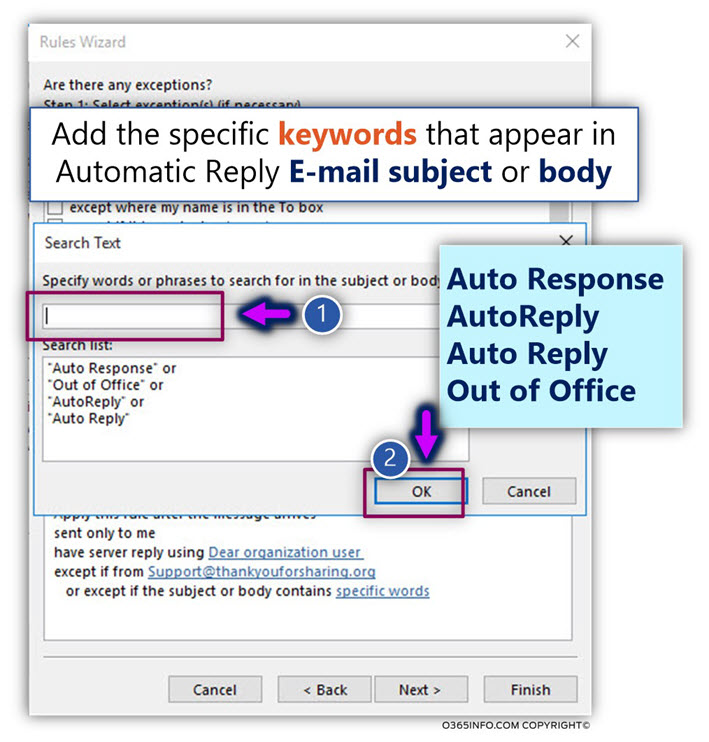
Step 2#3 – Adding an exception | Don’t reply if the E-mail subject or body includes specific keywords
In this section, we will create an additional mailbox rule exception that will try to “capture” incoming E-mail that has the characters of Automatic Reply E-mail.
For example, in many scenarios the Automatic Reply E-mail will include specific keywords such as:
- Auto Response
- AutoReply
- Auto Reply
- Out of Office
We will configure our mailbox rule exception to – try to recognize these specific
Keywords in the E-mail message or the E-mail body.
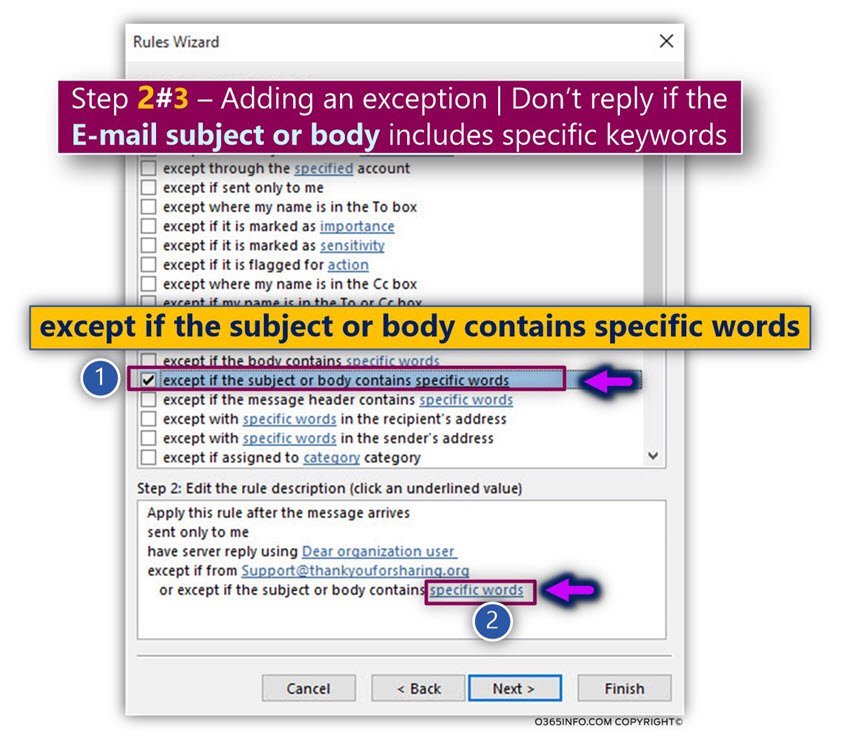
- Click on the link – specific words
- Select the check box – except if the subject or body contains specific words
![Detect and prevent a scenario of Mail loop -caused by Automatic reply – Exchange inbox rule -08 Detect and prevent a scenario of Mail loop -caused by Automatic reply – Exchange inbox rule -08]()
- Add the required keyword such as – Auto Response, AutoReply, Auto Reply, Out of Office.
- Click – OK
![Detect and prevent a scenario of Mail loop -caused by Automatic reply – Exchange inbox rule -09 Detect and prevent a scenario of Mail loop -caused by Automatic reply – Exchange inbox rule -09]()
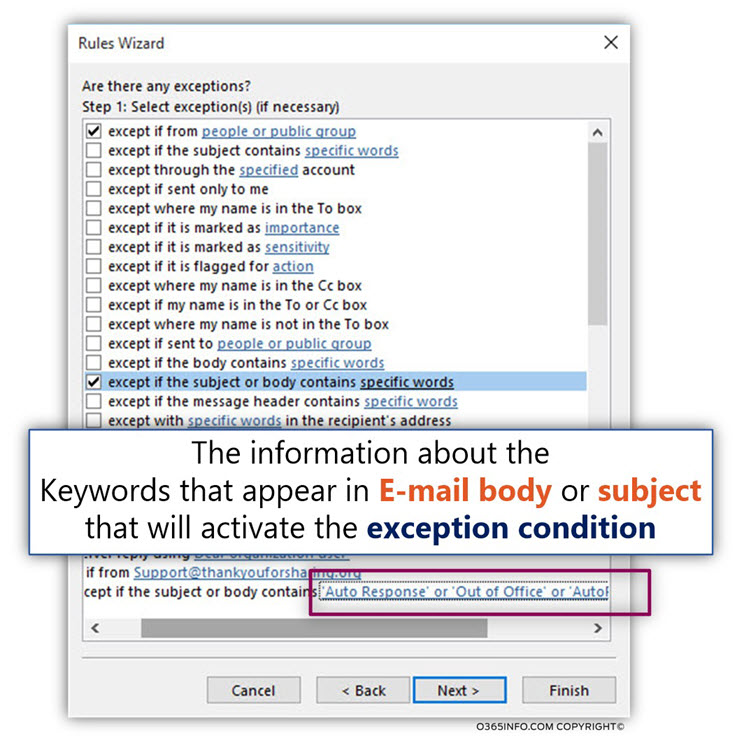
In the following screenshot, we can see that the information about the Keywords was updated in the mailbox rule exception section.
![Detect and prevent a scenario of Mail loop -caused by Automatic reply – Exchange inbox rule -10 Detect and prevent a scenario of Mail loop -caused by Automatic reply – Exchange inbox rule -10]()
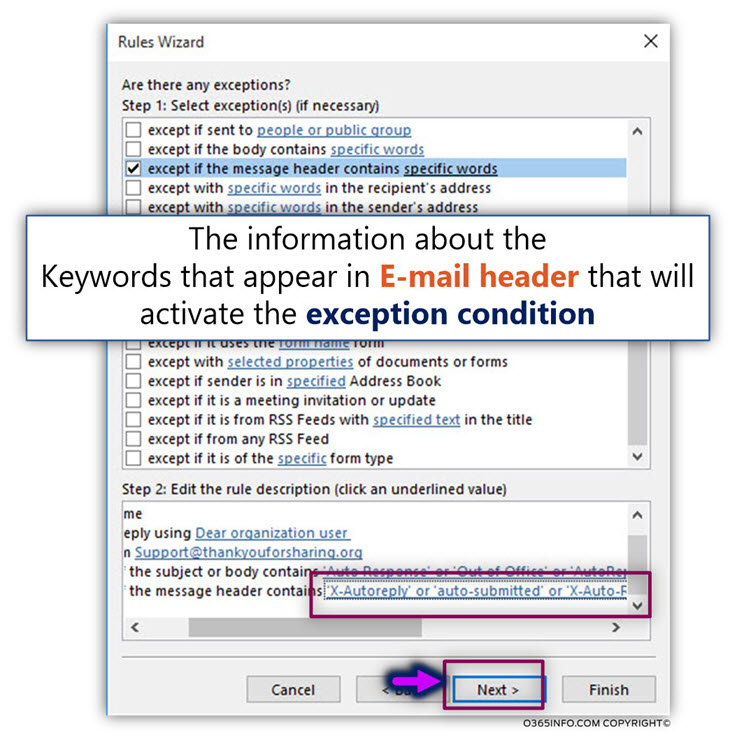
Step 3#3 – Adding an exception | Don’t reply if the E-mail header includes specific keywords
In this section, we will create an additional mailbox rule exception, that will try to “capture” incoming E-mail that has a specific mail field that are related to Automatic Reply E-mail.
For example, Exchange, and other mail server add the following mail fields to E-mail that considered as Automatic Reply E-mail:
- X-Autoreply
- auto-submitted
- X-Auto-Response-Suppress
- X-MS-Exchange-Inbox-Rules-Loop
We will configure our mailbox rule exception to – recognize these specific mail field’s keywords in the E-mail header.
- Click on the link – specific words
- Select the check box – except if the message header contains specific words
![Detect and prevent a scenario of Mail loop -caused by Automatic reply – Exchange inbox rule -11 Detect and prevent a scenario of Mail loop -caused by Automatic reply – Exchange inbox rule -11]()
- Add the required keyword such as – X-Autoreply, auto-submitted, X-Auto-Response-Suppress, X-MS-Exchange-Inbox-Rules-Loop
- Click – OK
![Detect and prevent a scenario of Mail loop -caused by Automatic reply – Exchange inbox rule -12 Detect and prevent a scenario of Mail loop -caused by Automatic reply – Exchange inbox rule -12]()
In the following screenshot, we can see that the information about the Keywords was updated in the mailbox rule exception section.
![Detect and prevent a scenario of Mail loop -caused by Automatic reply – Exchange inbox rule -13 Detect and prevent a scenario of Mail loop -caused by Automatic reply – Exchange inbox rule -13]()
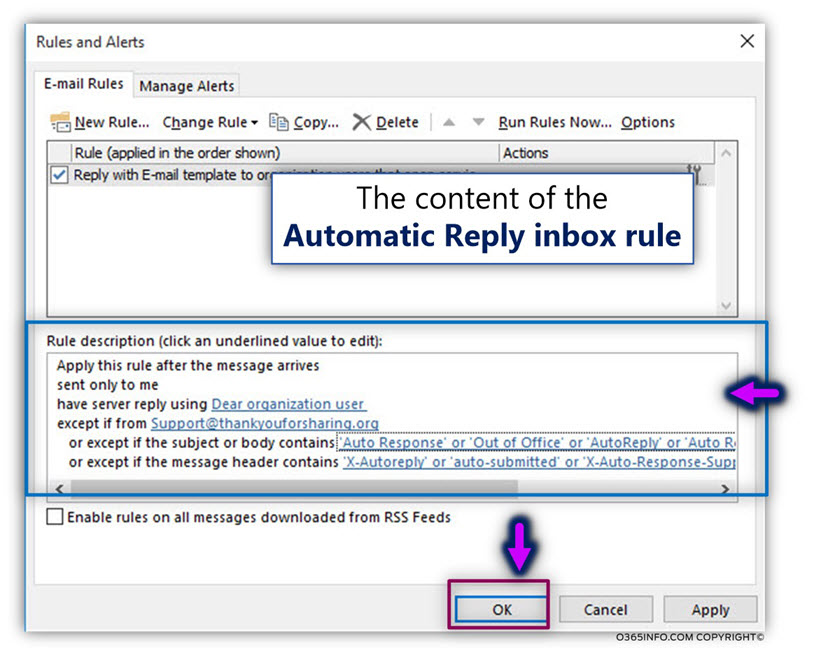
In the following screenshot, we can see the “summary” of the exceptions rules that were created.
![Detect and prevent a scenario of Mail loop -caused by Automatic reply – Exchange inbox rule -14 Detect and prevent a scenario of Mail loop -caused by Automatic reply – Exchange inbox rule -14]()
Manage Automatic Reply in Office 365 and Exchange Online article seriesArticle series index
Now it’s Your Turn!
It is important for us to know your opinion on this article
The post Automatic Reply in Office 365 -Dealing with mail loop (mail storm) scenarios |Part 7#7 appeared first on o365info.com.